Task 1 Introduction Outline
Deploy the machine.
No answer needed
Task 2 Getting Started What is Burp Suite?
Which edition of Burp Suite will we be using in this module?
"Burp Suite Community"
Which edition of Burp Suite runs on a server and provides constant scanning for target web apps?
"Burp Suite Enterprise"
Burp Suite is frequently used when attacking web applications and ______ applications.
"Mobile"
Task 3 Getting Started Features of Burp Community
Which Burp Suite feature allows us to intercept requests between ourselves and the target?
"Proxy"
Which Burp tool would we use if we wanted to bruteforce a login form?
"Intruder"
Task 4 Getting Started Installation
If you have chosen not to use the AttackBox, make sure that you have a copy of Burp Suite installed before proceeding.
No answer needed
Task 5 Getting Started The Dashboard
Open Burp Suite and have a look around the dashboard. Make sure that you are comfortable with it before moving on.
No answer needed
Task 6 Getting Started Navigation
Get comfortable navigating around the top menu bars.
No answer needed
Task 7 Getting Started Options
Change the Burp Suite theme to dark mode
No answer needed
In which Project options sub-tab can you find reference to a "Cookie jar"?
"Sessions"
In which User options sub-tab can you change the Burp Suite update behaviour?
"Misc"
What is the name of the section within the User options "Misc" sub-tab which allows you to change the Burp Suite keybindings?
"Hotkeys"
If we have uploaded Client-Side TLS certificates in the User options tab, can we override these on a per-project basis (Aye/Nay)?
"Aye"
There are many more configuration options available.
No answer needed
Task 8 Proxy Introduction to the Burp Proxy
Which button would we choose to send an intercepted request to the target in Burp Proxy?
"Forward"
[Research] What is the default keybind for this?
"Ctrl+F"
Task 9 Proxy Connecting through the Proxy (FoxyProxy)
The option is in a dropdown sub-menu.
"Response to this request"
[Bonus Question -- Optional] Try installing FoxyProxy standard and have a look at the pattern matching features.
No answer needed
Task 10 Proxy Proxying HTTPS
certificate for TLS communication through the Burp Proxy.
No answer needed
Using the in-built browser, make a request to http://MACHINE_IP/ and capture it in the proxy.
No answer needed
Add http://MACHINE_IP/ to your scope and change the Proxy settings to only intercept traffic to in-scope targets.
No answer needed
Task 13 Proxy Site Map and Issue Definitions
What is the flag you receive?
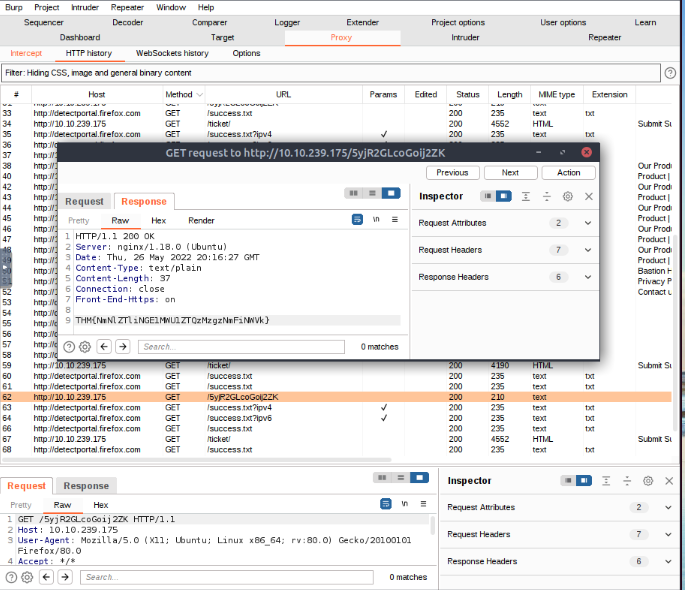
THM{NmNlZTliNGE1MWU1ZTQzMzgzNmFiNWVK}
Look through the Issue Definitions list. What is the typical severity of a Vulnerable JavaScript dependency?
"low"
Task 14 Practical Example Attack
Congratulations, you bypassed the filter!
No answer needed
Task 15 Conclusion Room Conclusion
I understand the fundamentals of using Burp Suite!
No answer needed