Extending Your Network
Task 1 Introduction to Port Forwarding
What is the name of the device that is used to configure port forwarding?
"router"
Task 2 Firewalls 101
What layers of the OSI model do firewalls operate at?
"Layer 3,Layer 4"
What category of firewall inspects the entire connection?
"stateful"
What category of firewall inspects individual packets?
"stateless"
Task 3 Practical – Firewall
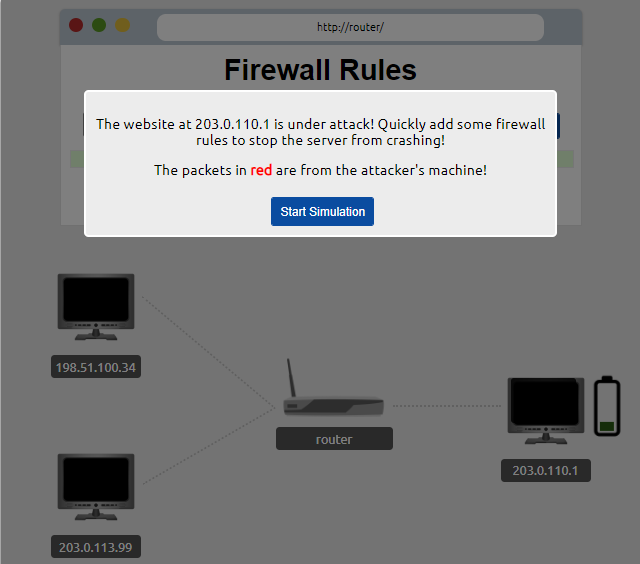
What we need to do at this stage is to protect our website from attack.
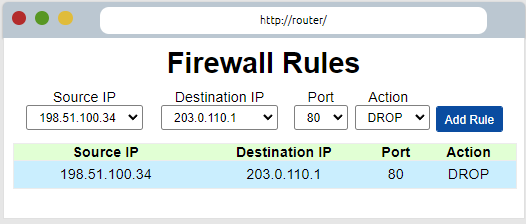
For the filter, we choose our source as the attacker's IP address. (198.51.100.34)
As the target filter, we choose our device that is exposed to the attack. (203.0.110.1)
As for the port, we choose 80 as we know that it is the website that has been hacked.
As an action, we set it as "DROP" as we will not let it pass.
Then we get our flag!
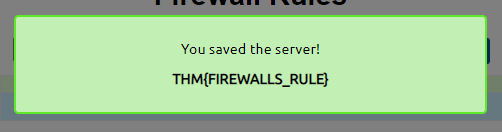
What is the flag?
"THM{FIREWALLS_RULE}"
Task 4 VPN Basics
What VPN technology only encrypts & provides the authentication of data?
"PPP"
What VPN technology uses the IP framework?
"IPSec"
Task 5 LAN Networking Devices
What is the verb for the action that a router does?
"routing"
What are the two different layers of switches? Separate these by a comma I.e.: LayerX,LayerY
"Layer2,Layer3"
Task 6 Practical – Network Simulator
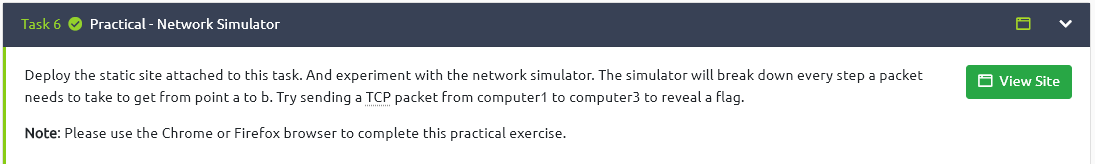
At this stage, as seen in the picture below, we enter the values requested from us and send a TCP packet to computer 3.
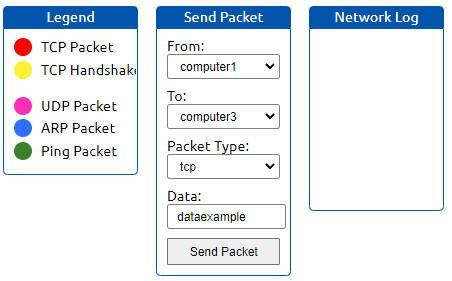
After sending our package, we get our flag.
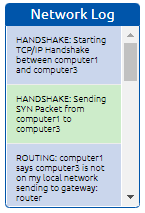
Another question asked to us is the number of handshakes.
We can count these values in Network Log.
What is the flag from the network simulator?
"THM{YOU'VE_GOT_DATA}"
How many HANDSHAKE entries are there in the Network Log?
"5"