First of all, we start by using Nmap, nikto, ffuz, tools to collect active information for the machine.
Nmap Output

ffuf Output
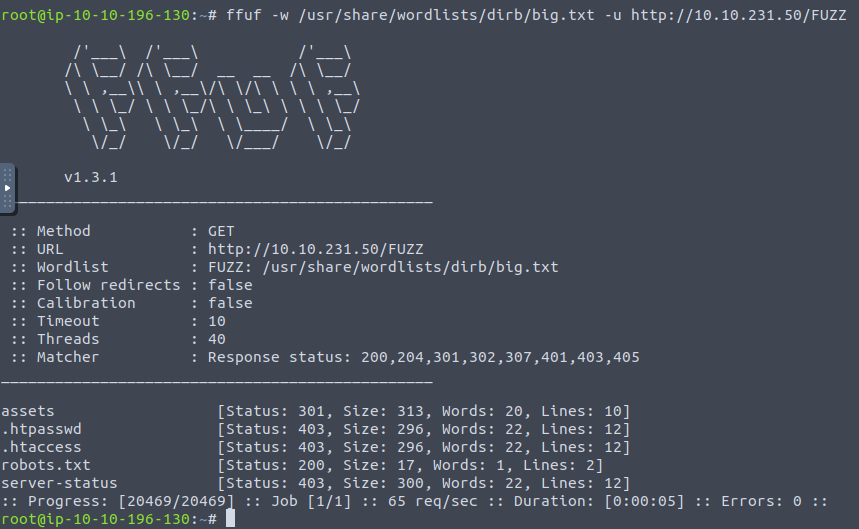
From the status codes in the ffuf output, we see that only the 'robots.txt' page is accessible.
The robots.txt page is as follows.

Nikto Output
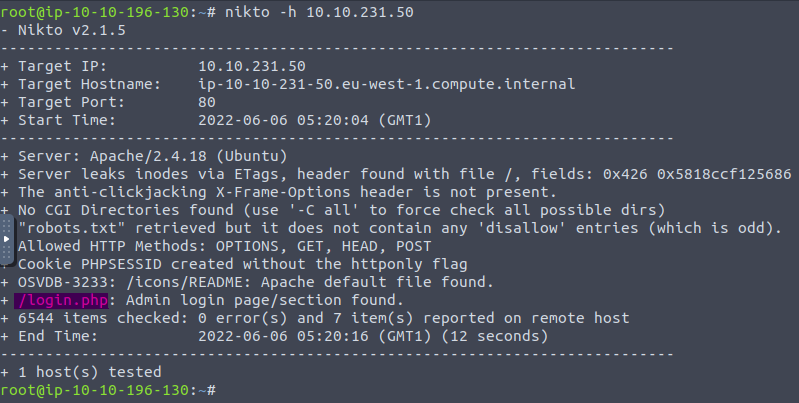
In the Nikto output, we see that there is a page named '/login.php' on the site.
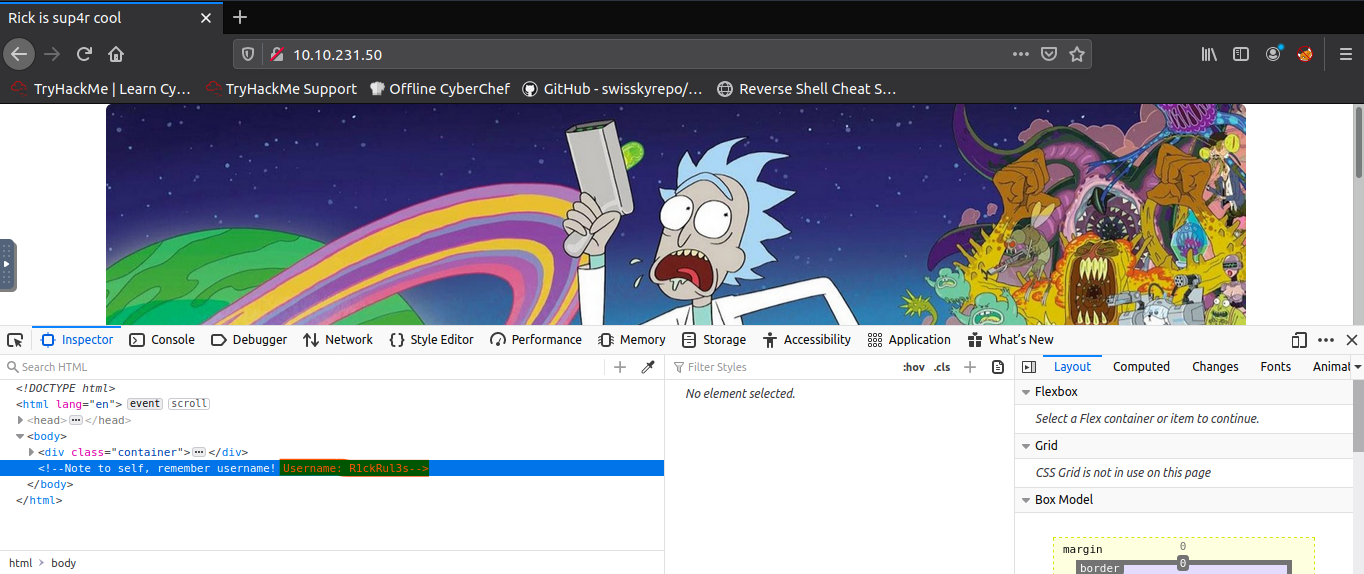
There is no useful information on the home page. But if we look at the source code, there is a username.
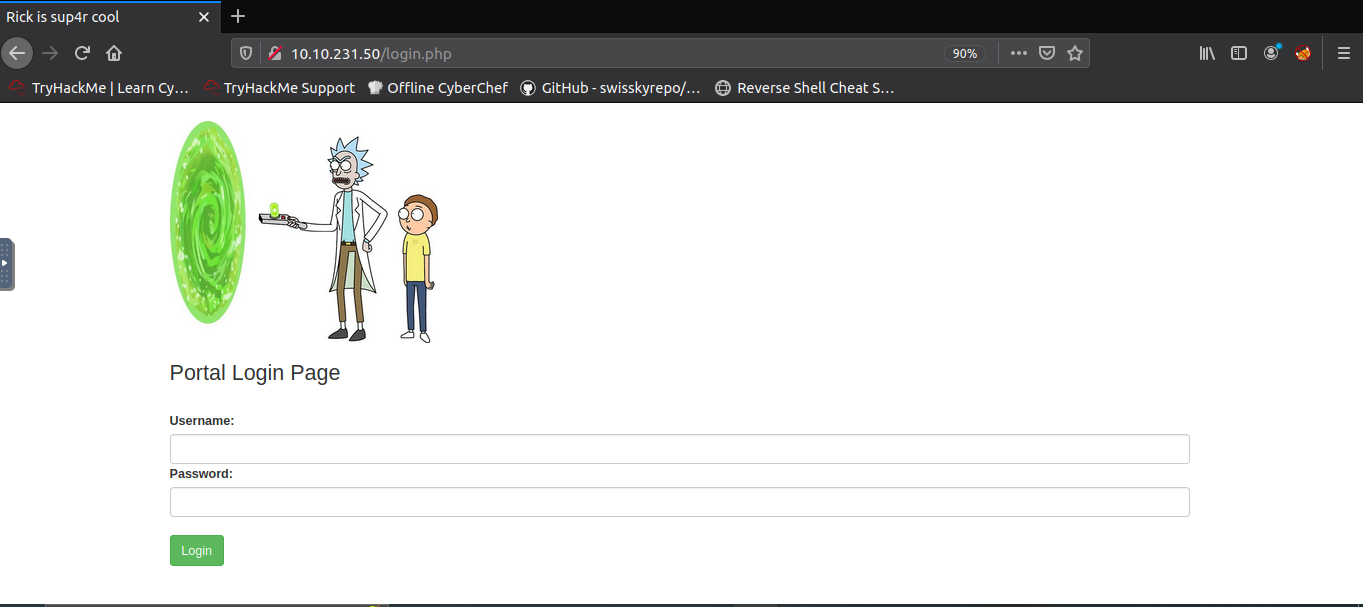
The 'login.php' page is as follows.
At this stage, I used tools such as burp and hydra to find the password, but I could not get a result.
then i remembered the robots.txt file
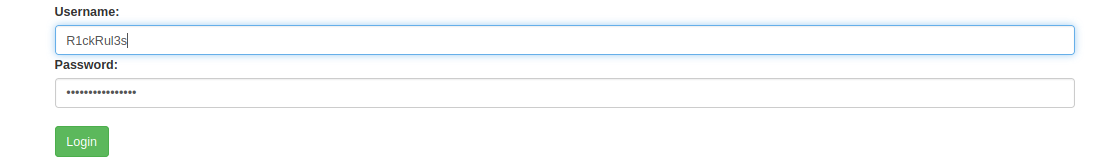
Login was successful when I tried…
When we log in, we see the command panel. As you can see in the picture below, we can run the code in it.

We see that the top file is one of the 3 files we are looking for.
Some commands like cat aren't allowed but you can read the first ingredient (flag) using for example less:

"mr. meeseek hair"
Thus, we get our 1st file.
In the command panel, when we browse the files a little, we see the file named rick as follows.

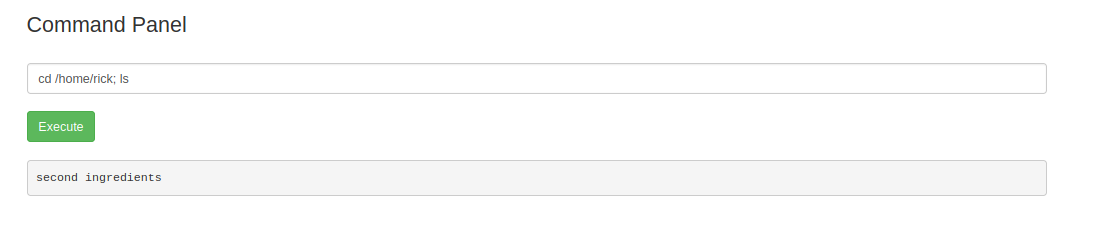
We also get our second file.

"1 jerry tear"

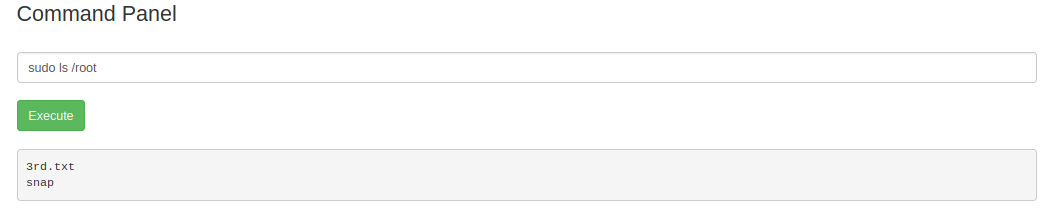
The user ‘www-data’ can execute anything as sudo:
So
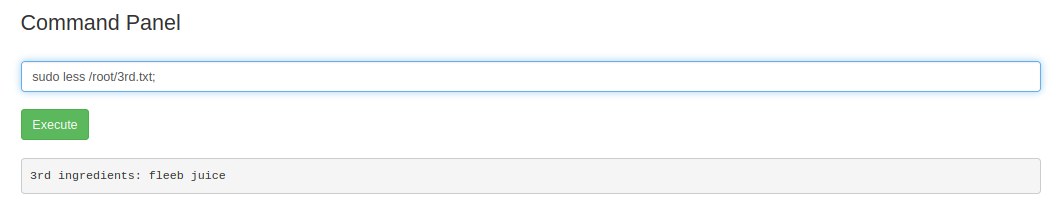
"fleeb juice"