

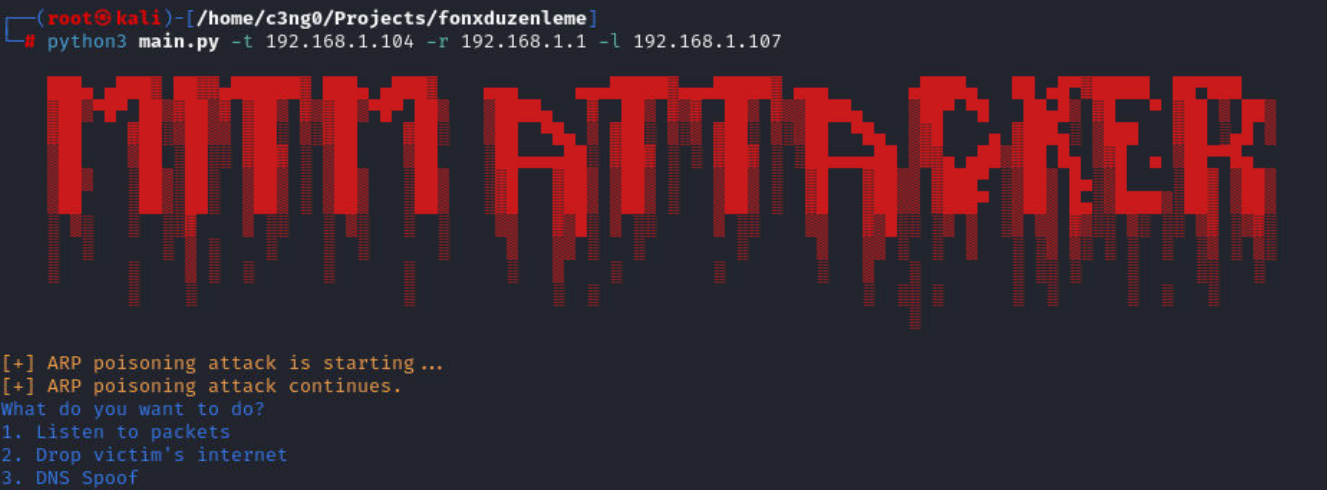
This project aims to execute a Man-in-the-Middle (MITM) attack in network security using a unified toolkit. The main Python-based application incorporates ARP Spoofing, DNS Spoofing, and Packet Sniffing techniques. Scapy is used for packet creation and analysis, while NetfilterQueue controls network traffic. Apache2 hosts fake web pages mimicking Instagram, Twitter, and Websiteos.
Below are the solutions of the CTF's I have solved.

Challenge showcasing a web app and simple privilege escalation. Can you find the glitch?
MoreBelow are the tools I learned and at the same time I wrote with the help of the internet.
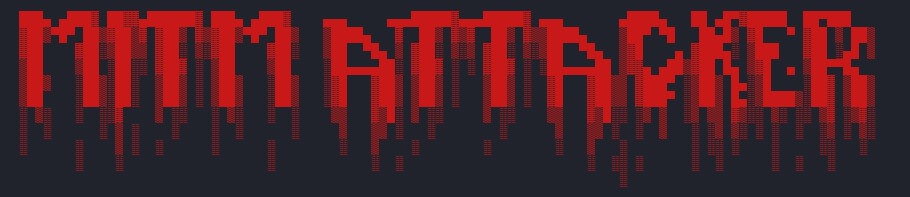
This project has been developed with the aim of executing a Man-in-the-Middle (MITM) attack in the field of network security.
More on Github
This script allows you to change the MAC address of a specified network interface on a Unix-like operating system.
More on Github
This script utilizes the Scapy library to perform network scanning by sending ARP requests to a specified IP address or IP range.
More on Github
This script performs ARP poisoning, also known as ARP spoofing, to manipulate the ARP tables of devices on a local network.
More on Github
The keylogger is designed as a simple demonstration for learning purposes. It records keyboard inputs and sends them via email at regular intervals.
More on Github
The packet listener is designed to capture HTTP packets and display their contents.
More on Github